In today’s hyperconnected digital world, cybercrime is no longer limited to suspicious emails or fake websites. Cybercriminals have evolved their tactics to exploit something far more personal and persuasive: the human voice. One of the most dangerous and increasingly common phone-based scams is known as vishing. Many people unknowingly fall victim to it because it sounds legitimate, urgent, and reassuring all at once.
This guide explains what is vishing, how it works, why it is so effective, and how you can protect yourself from becoming a victim. By understanding vishing attacks in depth, individuals and businesses can significantly reduce the risk of financial loss and identity theft.
What Is Vishing?

Vishing, short for voice phishing, is a type of social engineering attack where cybercriminals use phone calls or voice messages to trick victims into sharing sensitive information. This information may include banking details, credit card numbers, login credentials, personal identification data, or one-time verification codes.
In simple terms, vishing is also known as voice-based phishing, where attackers manipulate people through conversation rather than written messages. Unlike traditional phishing emails, vishing relies on verbal persuasion, emotional pressure, and impersonation to convince victims that the caller is trustworthy.
When people ask what is vishing?, the answer lies in understanding that it is not a technical attack but a psychological one. Attackers exploit fear, urgency, authority, and trust to achieve their goals.
Vishing Definition Explained Clearly
The vishing definition can be summarized as a fraudulent phone-based scam designed to deceive victims into voluntarily revealing confidential information or making payments. These scams often impersonate trusted entities such as banks, government agencies, technical support teams, or even law enforcement.
What makes vishing particularly dangerous is that victims often believe they are resolving a real issue. By the time they realize the truth, financial damage or identity theft may already have occurred.
How Vishing Works
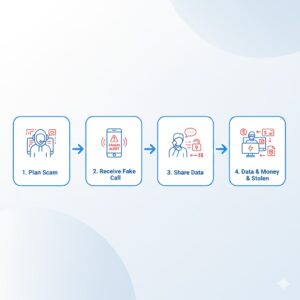
To fully understand what is vishing, it is important to see how a typical vishing attack unfolds.
A vishing attack usually begins with initial contact, either through a direct phone call or after the victim clicks a malicious link online. The attacker then creates a scenario that demands immediate attention. This could involve claims of suspicious bank activity, computer infections, unpaid taxes, or compromised accounts.
Once contact is established, the attacker adopts a calm and professional tone. They may claim to be a bank representative, a technical expert, or a government official. The goal is to build trust quickly and prevent the victim from questioning the situation.
As the conversation continues, the attacker pressures the victim into providing sensitive information or making a payment. This pressure is often reinforced with threats, such as account suspension, legal action, or permanent data loss.
Vishing in a Nutshell
Vishing often builds upon phishing. A victim might first encounter a fake email, advertisement, or warning message that prompts them to call a phone number. Once the call is made, the voice-based scam begins.
In many cases, malicious software triggers fake error messages that lock screens or display alarming alerts. These messages instruct victims to call a number for immediate assistance. On the other end of the line, the attacker poses as a helpful technician who claims to fix the problem for a fee.
The scam works because victims believe they are solving a serious issue rather than participating in fraud.
How Common Is Vishing?

Vishing is far more widespread than many people realize. Voice scams account for a significant portion of financial fraud worldwide. As phone numbers, personal details, and behavioral data become easier to obtain through data breaches and social media, attackers can craft highly convincing vishing attempts.
Cybercriminals often target individuals who may not be technologically savvy, but even educated professionals are vulnerable. Vishing attacks have successfully targeted employees, executives, retirees, and small business owners.
The growing reliance on mobile phones and remote communication has made vishing a preferred attack method for criminals seeking quick and profitable results.
Why Vishing Is So Effective
The success of vishing lies in human psychology. Unlike emails that can be scrutinized, phone conversations feel personal and immediate. Attackers use several tactics to manipulate victims effectively.
They create urgency by claiming immediate consequences if action is not taken. They exploit authority by impersonating trusted organizations. They use fear by suggesting financial loss, legal trouble, or data breaches. They also use reassurance, presenting themselves as helpful problem-solvers.
Because conversations happen in real time, victims often do not have enough time to verify information or think critically. This emotional manipulation is what makes vishing extremely effective.
Common Types of Vishing Scams
Vishing scams can take many forms, but they generally follow similar patterns.
One common type involves fake technical support calls where attackers claim the victim’s computer or phone is infected. Another involves banking scams, where callers warn of suspicious transactions and request verification details.
There are also government impersonation scams where attackers claim unpaid taxes or legal issues. Some scams even involve callers pretending to be distressed family members asking for urgent financial help.
Regardless of the scenario, the objective remains the same: to extract sensitive information or money.
How to Recognize Vishing Scams
Recognizing vishing early can prevent serious consequences. While scammers are becoming more sophisticated, there are warning signs that should never be ignored.
Unsolicited calls demanding immediate action are a major red flag. Legitimate organizations rarely pressure customers over the phone. Requests for sensitive information such as passwords, PINs, or full card numbers are another strong indicator of vishing.
Callers who refuse verification or discourage independent confirmation should not be trusted. Emotional manipulation, threats, and fear-based messaging are also common signs of vishing attempts.
Red Flags You Should Never Ignore
Any caller claiming you must act immediately should be treated with caution. Unexpected calls offering refunds, prizes, or technical fixes are often scams.
Links sent during calls via text or email should never be clicked. Attachments, remote access requests, or instructions to install software are also serious warning signs.
If something feels rushed, intimidating, or unusually secretive, it is best to end the call immediately.
What to Do If You Suspect Vishing
If you believe you are being targeted by a vishing scam, the first step is to stop engaging. Do not share any information, no matter how convincing the caller sounds.
Hang up the call and take time to verify the situation independently. Contact the organization directly using official contact details from trusted sources. Never use phone numbers provided by the caller.
If personal or financial information has already been shared, immediate action should be taken to secure accounts and monitor transactions.
Also Read:How to Remove a Hacker from Your Smartphone
Reporting Vishing Scams
Reporting vishing incidents helps protect others and assists authorities in tracking fraudulent activities. Victims should report scams to consumer protection agencies, financial institutions, and cybercrime reporting platforms.
Banks and service providers can help mitigate losses if they are informed early. Monitoring account activity closely after a suspected vishing incident is essential.
How to Prevent Vishing Attacks
Prevention starts with awareness. Understanding what is vishing and how it works is the strongest defense. Being skeptical of unsolicited calls and verifying all requests independently significantly reduces risk.
Limiting personal information shared online also reduces the data attackers can exploit. Regularly reviewing privacy settings on social platforms and being cautious with unknown calls can make a major difference.
Educating family members, employees, and colleagues about vishing ensures collective protection against these scams.
Why Vigilance Matters
Vishing scams are unlikely to disappear. As technology advances, attackers will continue to refine their methods. Staying informed, calm, and skeptical is the most effective way to protect yourself.
Remember that legitimate organizations will never pressure you into sharing sensitive information over the phone. Taking time to verify can prevent financial loss and emotional distress.
Conclusion
Vishing is one of the most deceptive and psychologically manipulative forms of cybercrime. By understanding what is vishing, recognizing warning signs, and practicing safe communication habits, individuals can significantly reduce their risk.
Knowledge is the most powerful defense. When users remain vigilant and informed, vishing scams lose their effectiveness. Protecting yourself starts with awareness, skepticism, and the willingness to pause before acting.
FAQs
What is vishing?
Vishing is a phone-based scam where attackers impersonate trusted entities to steal personal or financial information.
Vishing is also known as what?
Vishing is also known as voice phishing.
How is vishing different from phishing?
Phishing uses emails or messages, while vishing relies on voice calls and verbal manipulation.
Can vishing lead to identity theft?
Yes, stolen information from vishing can be used for identity theft and financial fraud.
How can I stay safe from vishing?
Avoid sharing information over unsolicited calls, verify independently, and remain cautious of urgent requests.




