Ransomware attacks have evolved rapidly over the years. What started as simple file encryption campaigns has transformed into highly organized cybercrime operations that target businesses, governments, and major enterprises. Among the most well-known examples of this evolution is Maze ransomware.
Maze ransomware became infamous because it didn’t just lock files and demand payment. It introduced a more aggressive method of extortion that changed the ransomware landscape forever. Instead of relying only on encryption, Maze attackers also focused on stealing data and threatening to expose it publicly. This created a dangerous situation for victims, because even if they restored systems from backups, they still faced the risk of confidential data being leaked.
In this guide, you will learn what Maze ransomware is, how it works, how it spreads, what major incidents it caused, whether paying the ransom is ever a good idea, and how individuals and organizations can protect themselves from similar threats.
Maze Ransomware
Maze ransomware is a type of malicious software designed to infiltrate computer systems, encrypt important files, and demand a ransom payment from the victim. What made Maze different from many older ransomware families is how it applied pressure. Instead of only threatening to keep files locked, Maze attackers often stole sensitive data first and later threatened to publish it if the ransom wasn’t paid.
This shift made Maze ransomware especially harmful to businesses because companies were no longer only dealing with operational shutdowns. They were also facing potential public embarrassment, legal trouble, customer trust issues, and financial penalties due to leaked data.
In short, the meaning of Maze ransomware goes beyond file locking. It represents a ransomware approach that combines system disruption + data theft + public blackmail, making it far more damaging than traditional ransomware.
What is Maze Ransomware?

To understand what Maze ransomware really is, it helps to see it as more than just a malicious program. Maze was part of a professional cybercriminal ecosystem where attackers operated like an organized business.
Maze ransomware targeted organizations that were likely to pay large sums quickly. These were usually businesses with high-value data or essential services. Instead of attacking random individuals at scale, Maze attacks were often focused, planned, and disruptive.
Maze ransomware became one of the most recognized ransomware names because it popularized a model known as double extortion.
Double extortion means the attackers do two things:
They encrypt data and block access to systems
They steal sensitive information and threaten to leak it
This two-layer pressure is what made Maze ransomware terrifying for many organizations. Even when companies had reliable backups, they still had to consider reputational and compliance damage from stolen data.
How Does Maze Ransomware Work?
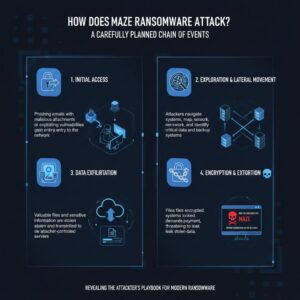
Understanding how Maze ransomware works is important because it reveals why it was so effective, and why ransomware attacks today often follow a similar playbook.
A Maze ransomware attack typically follows a carefully planned chain of events. The attackers don’t just “drop a virus and hope.” They often spend time inside the network before triggering encryption. This allows them to explore systems, locate critical files, and steal valuable information.
Here’s how the Maze ransomware process usually unfolds in practical terms.
Initial Entry Into the System
Maze ransomware often enters a target network through weak points such as phishing emails, exposed remote access tools, software vulnerabilities, or stolen credentials. Once access is gained, the attackers begin expanding control.
Instead of immediately encrypting files, they often try to stay hidden as long as possible. This gives them time to understand the organization’s infrastructure and identify what matters most.
Establishing Control and Privilege Escalation
After gaining access, attackers typically attempt to increase their permissions. They try to move from a standard user account to admin-level control. This stage is important because it enables the attackers to disable security tools, access more systems, and spread across the network.
Once inside at a deeper level, attackers can do far more damage and make recovery harder.
Data Discovery and Theft
One of the most dangerous parts of a Maze ransomware incident is the data theft stage. Attackers search for confidential information such as:
Customer records
Employee data
Financial files
Legal documents
Internal emails
Contracts and intellectual property
Once found, the information is copied and sent to attacker-controlled systems. This stage often happens quietly, without immediate signs that anything is wrong.
Encryption and System Lockdown
After stealing data and gaining enough control, Maze ransomware begins the encryption phase. During this stage:
Critical business files become unreadable
Systems stop functioning normally
Employees lose access to necessary data
Operations may come to a complete halt
Encryption is usually designed to be fast, damaging, and difficult to reverse without the attacker’s decryption key.
Ransom Note and Threats
Once the files are encrypted, Maze ransomware typically displays or drops a ransom note. The note may include:
Instructions for contacting the attackers
Payment demands (often in cryptocurrency)
Deadlines and escalation threats
Warnings about publishing stolen data
This is where Maze became different. Older ransomware only threatened file loss. Maze threatened both file loss and public exposure.
Maze is Typically Distributed Through:
Maze ransomware did not rely on only one method to reach victims. Like many advanced ransomware families, it spread through multiple techniques. This is why organizations needed layered security, not just one protective tool.
Below are the most common ways Maze ransomware was distributed.
Also Read: What Is Authorization vs Authentication?
Phishing Emails and Malicious Attachments
One of the most common entry methods is phishing. Attackers send emails that look authentic, often pretending to be:
A client
A supplier
A manager or coworker
A delivery company
A bank or finance department
The email may contain an attachment such as a document or archive file. Once opened, it can trigger malware download or install a loader that eventually delivers Maze ransomware.
Malicious Links and Fake Login Pages
Instead of attachments, attackers may use links that appear to lead to:
Account verification pages
Invoice portals
Shared documents
Password reset pages
These links may install malware silently or steal credentials, allowing attackers to gain network access.
Exploiting Outdated Software
Maze ransomware attacks often succeeded because organizations used outdated systems. When operating systems, web apps, or internal software are not updated, known vulnerabilities remain open.
Attackers actively scan the internet for systems running vulnerable versions. When they find one, they exploit it to gain entry and deploy malware.
Remote Desktop Exploits and Weak Credentials
Remote access tools such as Remote Desktop can be extremely risky when not secured properly. If a company exposes remote access to the internet and uses weak passwords, attackers can brute-force their way in.
Once they obtain access, they can move through the network and deploy Maze ransomware across multiple machines.
Trojan Loaders and Malware Bundles
Many ransomware attacks do not start with ransomware directly. Instead, they begin with other malware infections, such as:
Credential stealers
Remote access tools
Backdoors
Malware that downloads additional payloads
This staged method allows attackers to build control before delivering Maze ransomware.
Maze Ransomware Website
Maze ransomware became widely known because of its public data-leak strategy. In many cases, the attackers operated a leak platform where they published stolen documents if victims refused to pay.
This created a major fear factor for businesses. Even if they restored systems from backup, they still faced the risk of:
Sensitive client data becoming public
Confidential contracts being exposed
Internal communications being leaked
Regulatory action due to privacy laws
Loss of trust from customers and partners
This public leak method became a blueprint for many ransomware groups that appeared later. It proved that ransomware wasn’t just about blocking access anymore. It was also about controlling and threatening exposure.
The End for Maze Ransomware?
Many people ask whether Maze ransomware still exists today. While Maze as a name was reported to have ended or shut down its operations, the most important thing to understand is this:
Even when one ransomware brand disappears, its methods live on.
Cybercriminal groups often rebrand, split into different groups, or start new ransomware variants with similar strategies. The double extortion model that Maze popularized continues to be used widely across modern ransomware operations.
So, while Maze ransomware itself may not operate under the same identity, its impact is still present in how ransomware works today.
Maze Ransomware Attacks – Examples
Maze ransomware attacked several major organizations, and each attack demonstrated how serious ransomware can be when it targets high-value systems. These incidents helped shape public awareness and influenced how businesses began preparing for ransomware attacks.
Below are some widely discussed Maze ransomware examples and why they matter.
Cognizant Maze Ransomware Attack
The Cognizant Maze ransomware incident highlighted how ransomware can disrupt large global service providers. When a major IT services company is affected, the damage can spread beyond the company itself.
Clients may experience service delays or interruptions. Internal teams may struggle to restore systems quickly. The incident also showed how ransomware can cause ripple effects across supply chains.
Canon Maze Ransomware Attack
The Canon Maze ransomware event became a clear reminder that even highly recognizable global brands are not immune. When large organizations are targeted, the result is not only technical disruption but also media attention and customer anxiety.
This type of attack is dangerous because it can interrupt workflows and slow down operations at scale.
Xerox Maze Ransomware Attack
Xerox being associated with Maze ransomware demonstrated that ransomware is not limited to certain industries. Any company with valuable data, valuable infrastructure, or complex enterprise environments can become a target.
This case reinforced how important cybersecurity planning is, even for organizations that appear stable and well-established.
City of Pensacola Maze Ransomware Attack
When Maze ransomware impacts a city or municipal system, the consequences go beyond business operations. Local services may be delayed, essential workflows may stop, and citizens may be affected.
Government institutions often face challenges such as:
Legacy software systems
Limited cybersecurity budgets
High operational dependence on internal networks
High-value data such as public records
This makes them attractive targets for ransomware operations like Maze.
Should You Pay the Ransom for Maze Ransomware Attacks?
This is one of the hardest questions victims face during a ransomware incident. When business operations are stopped, pressure is intense. However, paying the ransom has serious risks.
Paying Does Not Guarantee Recovery
Even if a payment is made, attackers may:
Send a broken decryption tool
Delay responses
Demand additional payments
Disappear entirely
Victims may lose both money and data.
It Encourages More Attacks
Every successful payment supports the ransomware economy. It funds future attacks and motivates cybercriminals to continue targeting businesses.
You Might Still Face Data Leaks
Even if you pay, attackers might still publish the stolen data later. The victim has no real control after paying because the criminals decide what happens next.
Legal and Compliance Risks
Some organizations may face legal issues depending on where they operate and who the attackers are. Even without legal consequences, paying the ransom could raise major compliance concerns.
The safer approach is always prevention first, then strong response planning, backups, and rapid recovery procedures.
How to Protect Against Maze Ransomware
Although Maze ransomware itself might not be as active as it once was, the same techniques still exist in many modern ransomware attacks. That’s why learning how to protect against Maze ransomware is still valuable today.
Keep Software and Operating Systems Updated
Unpatched systems are one of the easiest entry points for ransomware. Updates often include:
Security patches
Bug fixes
Vulnerability closures
Delaying updates creates a window of opportunity for attackers.
Use Security Software
A strong security setup should monitor:
Malicious downloads
Suspicious email attachments
Unusual system activity
Unauthorized access attempts
Security tools help detect threats earlier, which reduces the chance of a full ransomware outbreak.
Use VPN to Access the Network
Remote work and remote access tools are common entry points. A secure VPN can:
Encrypt communication
Reduce exposure of network services
Protect users connecting from public networks
VPN use should be combined with strong authentication policies.
Back Up Data
Backups are essential because they provide a recovery path without ransom payments. A strong backup strategy should include:
Regular backup schedules
Offline or isolated backup storage
Testing backups to confirm they work
Different backup versions to avoid restoring infected files
Educate and Inform Staff About Cybersecurity Risks
Many ransomware attacks begin with human error. Staff should be trained to spot:
Phishing emails
Fake links
Suspicious attachments
Urgency-based scams
Fake tech support messages
Awareness reduces the success rate of social engineering tactics.
FAQs
What is Maze ransomware in simple words?
Maze ransomware is a type of malware that encrypts files and demands money, often while also stealing data and threatening to leak it publicly.
How does Maze ransomware spread?
Maze ransomware spreads through phishing emails, malicious downloads, software vulnerabilities, and insecure remote access methods.
Why is Maze ransomware so dangerous?
Maze ransomware is dangerous because it combines encryption with data theft, which increases pressure on victims and creates long-term risks.
Can Maze ransomware be removed easily?
Removing ransomware is difficult once files are encrypted. The best solution is prevention and strong recovery planning like backups.
Is Maze ransomware still active today?
The Maze name may not be active in the same form, but the methods Maze used are still common in modern ransomware attack
Conclusion
Maze ransomware changed how the world understood ransomware attacks. It proved that cybercriminals do not need to rely only on file encryption to pressure victims. By adding data theft and leak threats, Maze ransomware created a model that made attacks more financially effective for criminals and far more damaging for victims.
Understanding what Maze ransomware is, how it spreads, and how it works helps individuals and organizations stay prepared. While the Maze ransomware group may not operate under the same identity today, the strategies it introduced remain a major part of modern cybercrime.
The best defense is not panic after an attack, but prevention before it happens. Strong updates, secure access controls, backups, and staff awareness are the real foundation of ransomware protection.




