Ransomware has evolved from simple file-locking malware into a sophisticated cybercrime ecosystem. Among the most dangerous and disruptive threats to emerge in recent years is CL0P ransomware (also written as cl0p ransomware). Known for targeting large organizations, exploiting zero-day vulnerabilities, and using double-extortion tactics, CL0P ransomware has caused widespread financial and reputational damage across industries.
In this in-depth guide, we’ll answer the critical question: what is CL0P ransomware, explore its history, understand how the CL0P ransomware group operates, and examine how organizations can prevent, detect, and respond to attacks effectively.
A Short History of CL0P Ransomware

CL0P ransomware first appeared around 2019, quickly distinguishing itself from other ransomware families due to its technical sophistication and strategic targeting. Initially, CL0P relied on phishing campaigns and compromised Remote Desktop Protocol (RDP) access to infiltrate networks.
Over time, the group evolved its tactics significantly. Instead of indiscriminate attacks, CL0P shifted toward high-value enterprise targets, focusing on organizations that store large volumes of sensitive data. This evolution marked CL0P’s transition into a double-extortion ransomware model, where attackers steal data before encrypting systems.
Major global incidents linked to cl0p ransomware involved the exploitation of file transfer and enterprise software vulnerabilities, allowing attackers to compromise hundreds of organizations simultaneously. These large-scale attacks solidified CL0P’s reputation as one of the most aggressive ransomware operators in the cybercrime landscape.
Also Read: Types of Biometrics
What Is CL0P Ransomware?
So, what is CL0P ransomware exactly?
CL0P ransomware is a type of malicious software designed to encrypt files, steal sensitive data, and extort victims for ransom payments. Unlike traditional ransomware that only locks data, cl0p ransomware threatens to publicly release stolen information if victims refuse to pay.
Key characteristics of cl0p ransomware include:
- Advanced encryption mechanisms
- Pre-encryption data exfiltration
- Targeted enterprise-level attacks
- Use of legal and psychological pressure tactics
- Public leak sites to shame non-paying victims
What sets cl0p ransomware apart is its emphasis on data theft over system disruption. In many cases, attackers exfiltrate massive datasets without deploying file encryption at all, relying solely on extortion threats to force payment.
Industries frequently targeted include finance, healthcare, manufacturing, education, logistics, and government-linked organizations.
Who Is Behind the CL0P Ransomware Group?
The CL0P ransomware group is believed to be a well-organized cybercriminal syndicate with deep technical expertise. While exact identities remain unknown, security researchers attribute CL0P to a group operating primarily out of Eastern Europe, with strong links to underground cybercrime forums.
The group operates using a Ransomware-as-a-Service (RaaS) model. This means core developers create and maintain the malware, while affiliates carry out attacks in exchange for a share of the ransom payments.
Key traits of the clop ransomware group include:
- High operational discipline
- Exploitation of zero-day vulnerabilities
- Strategic victim selection
- Public negotiation pressure
- Professionalized extortion methods
Rather than attacking random users, the CL0P ransomware group focuses on organizations with the financial capacity and legal exposure to feel pressured into paying ransoms.
CL0P Ransomware: How It Works
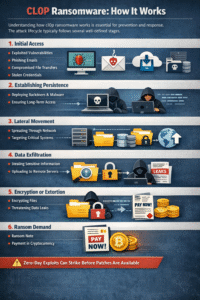
Understanding how cl0p ransomware works is essential for prevention and response. The attack lifecycle typically follows several well-defined stages.
1. Initial Access
CL0P commonly gains access through:
- Exploited software vulnerabilities
- Compromised file transfer platforms
- Phishing emails with malicious payloads
- Stolen or weak credentials
Zero-day exploitation is one of the most dangerous aspects of cl0p ransomware, as organizations may be compromised before patches are available.
2. Establishing Persistence
Once inside the network, attackers deploy scripts and backdoors to maintain long-term access. This allows them to operate silently without detection for weeks or even months.
3. Lateral Movement
The attackers then move laterally across the network, escalating privileges and identifying high-value systems such as:
- File servers
- Backup repositories
- Databases containing personal or financial data
4. Data Exfiltration
Before encryption begins, cl0p ransomware steals sensitive data. This may include:
- Customer records
- Intellectual property
- Financial documents
- Employee information
5. Encryption or Extortion
In some cases, files are encrypted. In others, attackers rely solely on data-leak extortion, threatening to publish stolen information on dark web leak sites.
6. Ransom Demand
Victims receive a ransom note demanding payment, often in cryptocurrency, with strict deadlines and escalating threats.
Preventing CL0P Ransomware
Preventing cl0p ransomware requires a multi-layered cybersecurity strategy. No single defense is sufficient against such advanced threats.
Key Prevention Measures
- Timely patch management for all software and third-party tools
- Email filtering and phishing protection
- Strong access controls and least-privilege policies
- Network segmentation to limit lateral movement
- Endpoint detection and response (EDR) solutions
- Offline and immutable backups
- Regular security awareness training for employees
Organizations should also conduct regular vulnerability assessments and penetration testing to identify weaknesses before attackers do.
Dealing With the CL0P Ransomware Virus
If an organization becomes infected, swift and structured action is critical.
Immediate Response Steps
- Isolate affected systems from the network
- Disable compromised accounts
- Preserve logs and evidence for investigation
- Notify internal security teams and leadership
Investigation and Recovery
- Conduct a full forensic analysis
- Identify entry points and data exfiltration scope
- Restore systems from clean backups
- Patch exploited vulnerabilities
Should You Pay the Ransom?
Paying ransom is risky and does not guarantee data recovery or deletion. It may also encourage future attacks. Many organizations choose recovery and mitigation over payment, especially when backups are available.
The Threat of CL0P Ransomware
The ongoing threat posed by cl0p ransomware is significant. Its ability to exploit supply chains and third-party software means even well-secured organizations can be affected indirectly.
Key risks include:
- Massive financial losses
- Regulatory penalties due to data exposure
- Long-term reputational damage
- Business interruption and loss of trust
As attackers continue refining their techniques, cl0p ransomware remains a persistent and evolving global cyber threat.
Frequently Asked Questions
What is CL0P ransomware?
CL0P ransomware is a sophisticated cyber extortion malware that steals sensitive data and encrypts systems to demand ransom payments from organizations.
How dangerous is cl0p ransomware?
Cl0p ransomware is extremely dangerous due to its use of zero-day exploits, data theft, and large-scale attacks on enterprises.
Who does the CL0P ransomware group target?
The clop ransomware group primarily targets medium to large organizations across finance, healthcare, manufacturing, and government-related sectors.
Can cl0p ransomware be removed without paying ransom?
Yes, if backups exist and systems are properly restored. However, stolen data may still pose risks.
How can businesses prevent cl0p ransomware attacks?
Regular patching, strong access controls, employee training, backups, and advanced threat detection significantly reduce risk.
Conclusion
Understanding what is CL0P ransomware is no longer optional for modern organizations. As one of the most advanced ransomware threats in existence, cl0p ransomware demonstrates how cybercrime has shifted toward strategic, data-driven extortion.
The CL0P ransomware group continues to exploit technical and human vulnerabilities, proving that prevention, preparedness, and rapid response are essential. By investing in proactive cybersecurity measures, regular updates, and incident response planning, organizations can significantly reduce their exposure to this evolving threat.
Debabrata Behera is a passionate blogger who writes about digital trends, personal growth, and practical insights, helping readers stay informed, inspired, and ready to achieve success in life.




