As organizations grow, managing who can enter specific areas becomes more complex and risky. Traditional locks, keys, and manual registers are no longer enough to protect offices, factories, hospitals, or campuses. Lost keys, shared access cards, and human errors can easily lead to security breaches.
Access control software plays a critical role in modern security systems by acting as the central system that decides who can enter, when they can enter, and where they are allowed to go. Instead of relying on physical control alone, organizations can use software-driven rules, real-time monitoring, and automated security actions to protect people, assets, and sensitive data. This blog explains the key features of access control software that directly enhance security and help organizations maintain better control over their premises.
What Is Access Control Software?
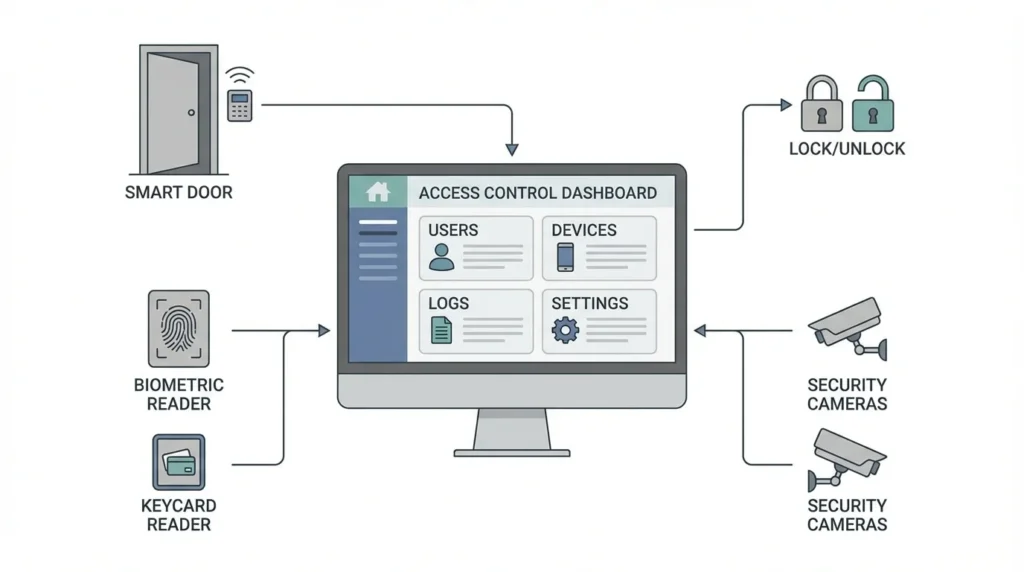
Access control software is the digital platform that manages, monitors, and controls access permissions within a secured environment. It works alongside hardware such as card readers, biometric devices, electronic locks, and controllers.
The software is responsible for defining access rules, verifying user credentials, and logging every access-related activity. While hardware handles the physical action of opening or locking doors, the software makes the actual security decisions. By centralizing access management, access control software ensures consistency, accuracy, and accountability across the entire security system.
How Access Control Software Enhances Overall Security
Access control software strengthens security by automating decisions and reducing reliance on manual processes. It ensures that access permissions are enforced consistently and instantly.
- Prevents unauthorized access by verifying credentials in real time
- Reduces security gaps caused by lost keys or shared access cards
- Improves visibility into movement across secured areas
- Creates accountability by linking access events to specific users
- Supports internal security policies and compliance requirements
Key Features of Access Control Software That Enhance Security
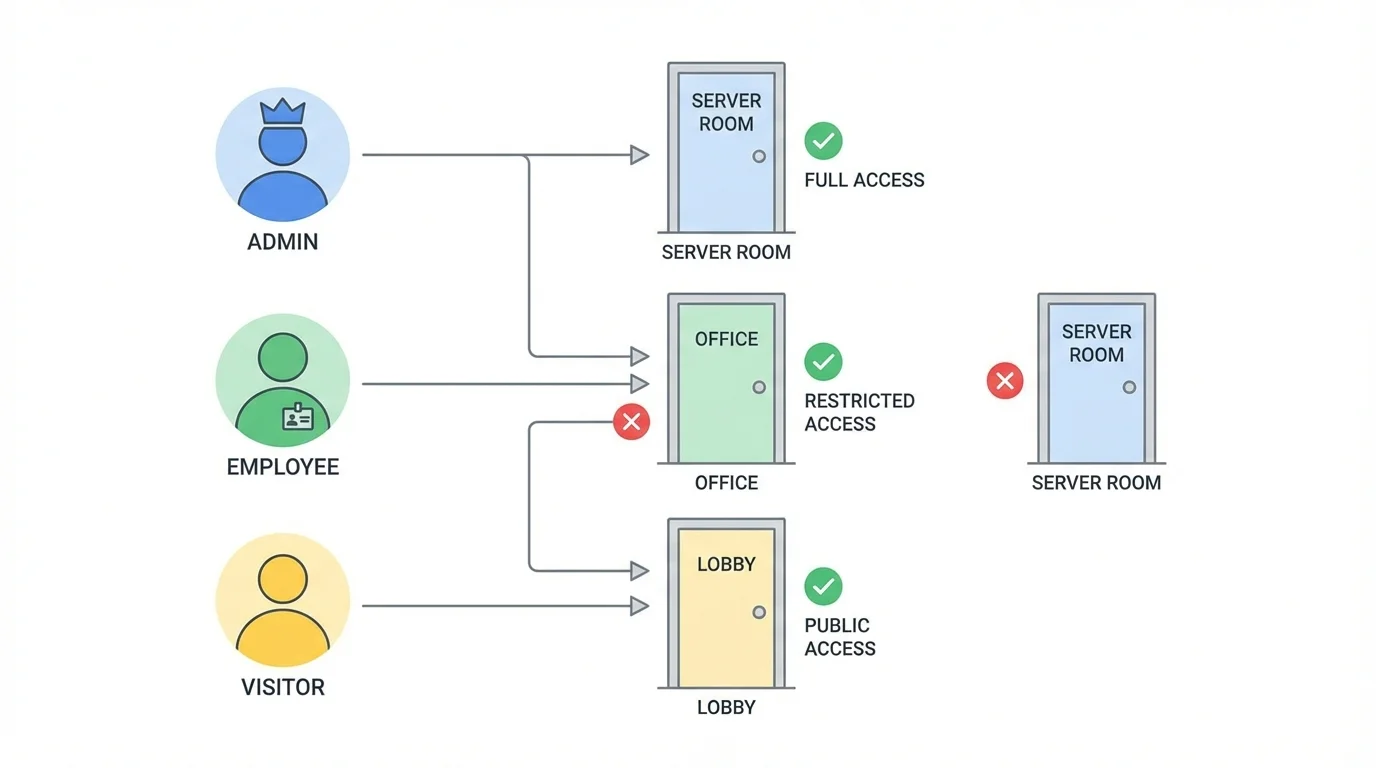
1. Role-Based Access Control (RBAC)
Role-based access control allows organizations to assign permissions based on a person’s job role rather than individual decisions for each user. This approach ensures that employees can only access areas required for their responsibilities.
- Limits access based on roles, departments, or designations
- Reduces the risk of internal misuse or accidental access
- Simplifies access management when employees join, move, or leave
- Ensures consistent security rules across similar job functions
2. Multi-Factor Authentication (MFA)
Multi-factor authentication adds an extra layer of security by requiring more than one form of verification before granting access. This makes it harder for unauthorized users to gain entry, even if one credential is compromised.
- Combines multiple authentication factors such as PINs, cards, or biometrics
- Reduces the risk of access through stolen or guessed credentials
- Strengthens security in sensitive or restricted areas
- Improves confidence in identity verification
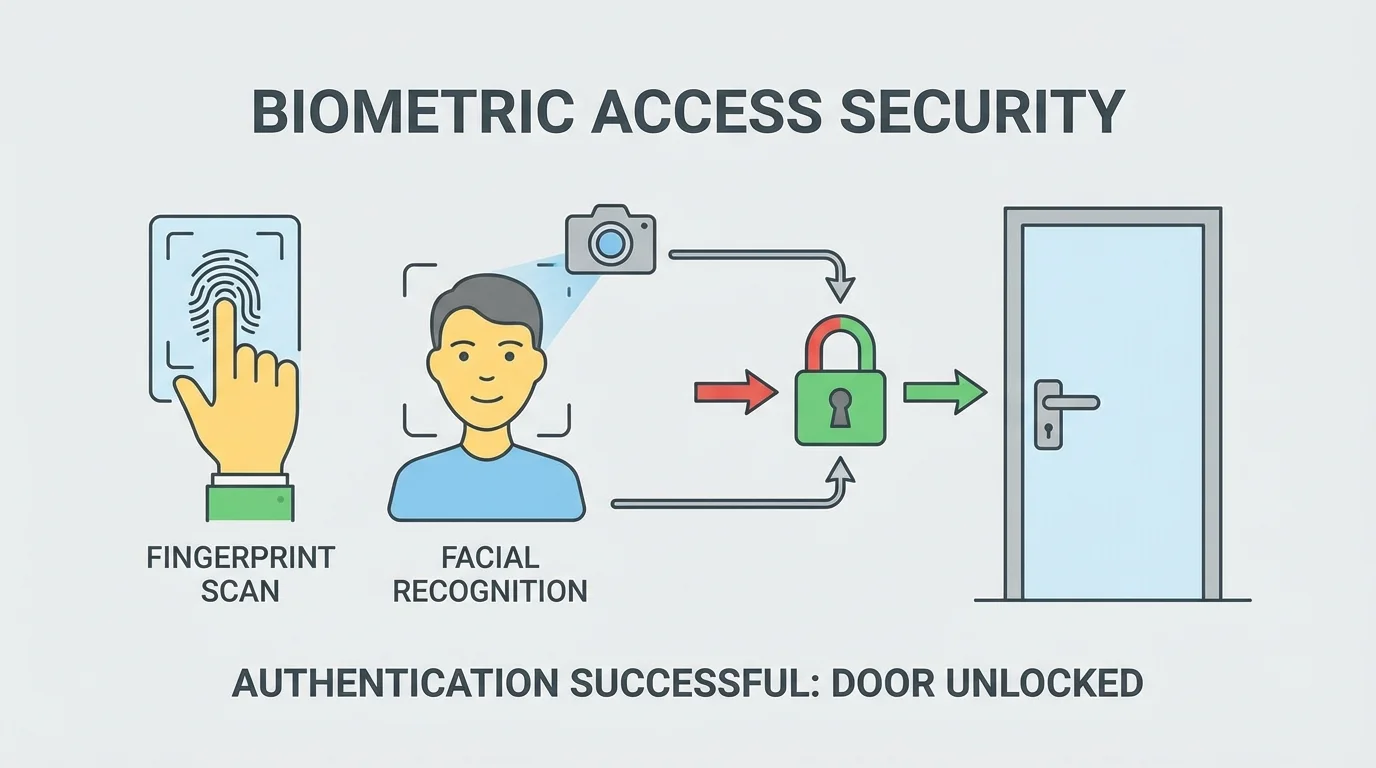
3. Biometric Integration
Biometric integration allows access control software to work with fingerprint, facial recognition, or iris scanning systems. These methods rely on unique physical characteristics that are difficult to copy or share.
- Eliminates risks associated with lost or shared credentials
- Improves accuracy in identifying authorized individuals
- Provides fast and convenient access without physical tokens
- Enhances security in high-risk or high-value locations
4. Real-Time Access Monitoring
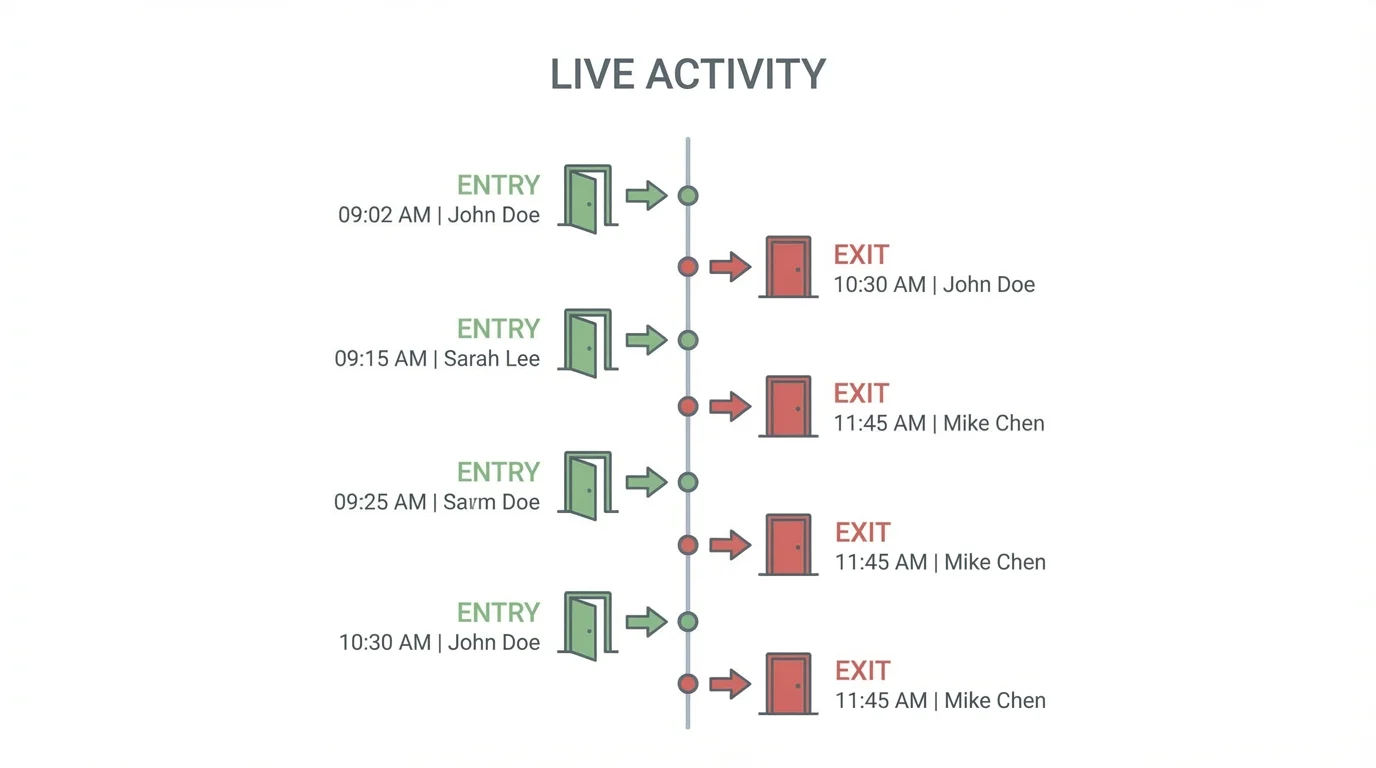
Real-time access monitoring enables security teams to see access activity as it happens. This immediate visibility helps detect unusual behavior and respond quickly to potential threats.
- Tracks entry and exit events across all access points
- Identifies unauthorized or repeated failed access attempts
- Provides instant awareness of security incidents
- Supports proactive security management
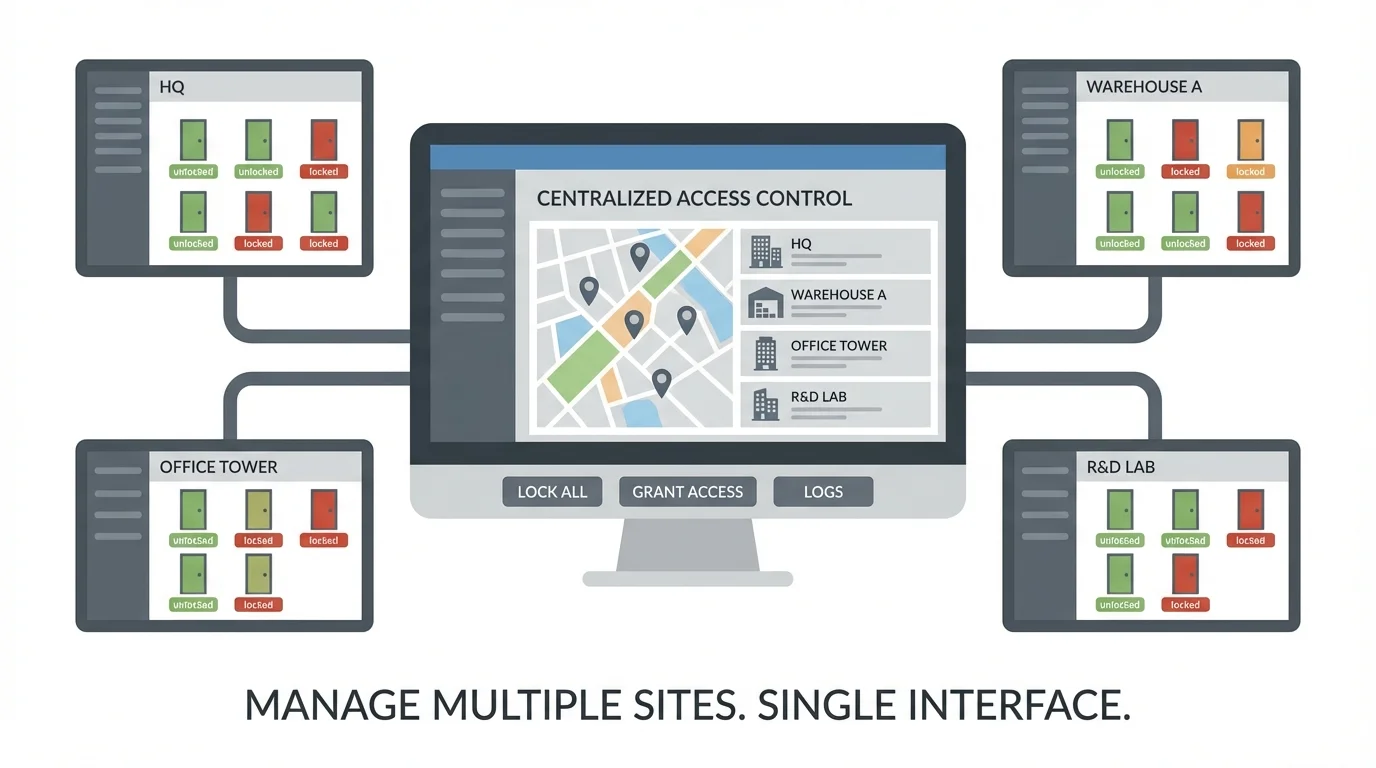
5. Centralized Access Management Dashboard
A centralized dashboard allows administrators to manage all access points, users, and permissions from one interface. This reduces complexity and improves control across the organization.
- Simplifies management of doors and users
- Reduces configuration errors and inconsistencies
- Enables faster updates to access permissions
- Supports security management across multiple locations
6. Detailed Audit Logs and Activity Reports
Audit logs record every access-related event, creating a detailed history of activity within the system. These records are essential for investigations, audits, and compliance.
- Logs successful and failed access attempts
- Tracks changes made to access permissions
- Provides evidence during security investigations
- Supports regulatory and internal audit requirements
7. Time-Based and Schedule-Based Access Control
Time-based access control restricts entry based on predefined schedules. This ensures that access is only allowed during approved times.
- Prevents unauthorized after-hours access
- Supports shift-based or temporary access needs
- Enhances security during non-working hours
- Reduces reliance on manual supervision
8. Remote Access Control and Management
Remote access control allows administrators to manage access permissions and doors from anywhere. This is especially useful for large or distributed organizations.
- Enables remote locking or unlocking of doors
- Supports quick response during emergencies
- Reduces delays in access updates
- Improves security oversight across locations
9. Alerts and Notifications for Security Events
Alerts and notifications inform security teams immediately when unusual or risky events occur. This helps reduce response time and limit potential damage.
- Sends alerts for failed access attempts
- Notifies teams of forced entry or suspicious behavior
- Allows customization of alert thresholds
- Improves incident response speed
10. Integration with Other Security Systems
Access control software becomes more powerful when integrated with other security systems such as video surveillance and alarms. Integration creates a unified security environment.
- Links access events with video footage
- Improves incident verification and investigation
- Enables coordinated security responses
- Reduces gaps between separate security systems
11. Anti-Passback and Tailgating Prevention
Anti-passback features prevent users from sharing credentials or entering restricted areas improperly. These controls help stop common access control violations.
- Prevents reuse of credentials without exit confirmation
- Reduces risks of unauthorized sharing
- Discourages tailgating and piggybacking
- Enhances security in sensitive zones
12. Visitor and Temporary Access Management
Visitor management features ensure that guests and temporary users are granted controlled and limited access without compromising security.
- Issues time-limited access permissions
- Restricts visitor access to specific areas
- Improves tracking of non-employee movement
- Reduces security risks from unmanaged visitors
Security Benefits of Using Advanced Access Control Software
Advanced access control software provides a stronger and more reliable security framework for organizations of all sizes.
- Minimizes unauthorized access risks
- Improves accountability and transparency
- Enhances response to security incidents
- Strengthens audit readiness and compliance
Industries That Benefit Most from Secure Access Control Software
Different industries face unique security challenges, and access control software helps address them effectively.
- Corporate offices protecting employees and data
- Healthcare facilities securing patients and records
- Manufacturing plants controlling operational areas
- Educational institutions managing campus access
- Data centers protecting critical infrastructure
How to Choose Access Control Software with the Right Security Features
Selecting the right access control software requires a clear understanding of security needs and future requirements.
- Identify critical security features based on risk level
- Ensure scalability for future growth
- Balance ease of use with security depth
- Evaluate vendor reliability and system updates
Conclusion
Access control software is a critical component of modern security strategies. By combining intelligent access rules, real-time monitoring, detailed reporting, and system integrations, it helps organizations protect their people, assets, and data more effectively. Choosing software with the right security-focused features ensures stronger control, reduced risks, and better preparedness for future security challenges.