In today’s digital landscape, where information flows across global networks every second, data protection has become one of the most important challenges for individuals, businesses, and governments alike. Every message sent, every online purchase made, and every file stored in the cloud involves data being transferred through various networks. Without the right security measures, this data can easily be intercepted or manipulated by unauthorized parties. That is where data encryption comes into play.
Encryption acts as a digital shield that transforms readable information into unreadable code, protecting it from hackers and cybercriminals. It is one of the foundational tools in modern cybersecurity, ensuring the confidentiality and integrity of data across all platforms. Just as understanding cryptocurrency concepts requires knowledge of how cryptography and blockchain protect financial transactions, understanding encryption is essential for grasping how data privacy is maintained in cyberspace.
This blog will explore what is data encryption, how it works, its types, methods, real-world examples, and its benefits in securing digital communication and storage.
Encryption: Definition and Meaning
Encryption, in its simplest form, is the process of converting readable data (known as plaintext) into an unreadable or scrambled form (ciphertext). This process is performed using mathematical algorithms and cryptographic keys, which determine how the data is encoded and decoded. Only someone who possesses the correct key can decrypt the ciphertext back into its original form.
In cybersecurity, encryption ensures that sensitive information — such as passwords, credit card details, or personal messages — cannot be accessed or understood by unauthorized individuals, even if the data is intercepted.
In essence, encryption is to data what crypto currency meaning is to digital finance — a way of securing valuable information using mathematical principles. Just as what is crypto refers to a digital form of currency secured through cryptographic functions, encryption relies on similar technologies to secure communication and digital assets.
How Encryption Works
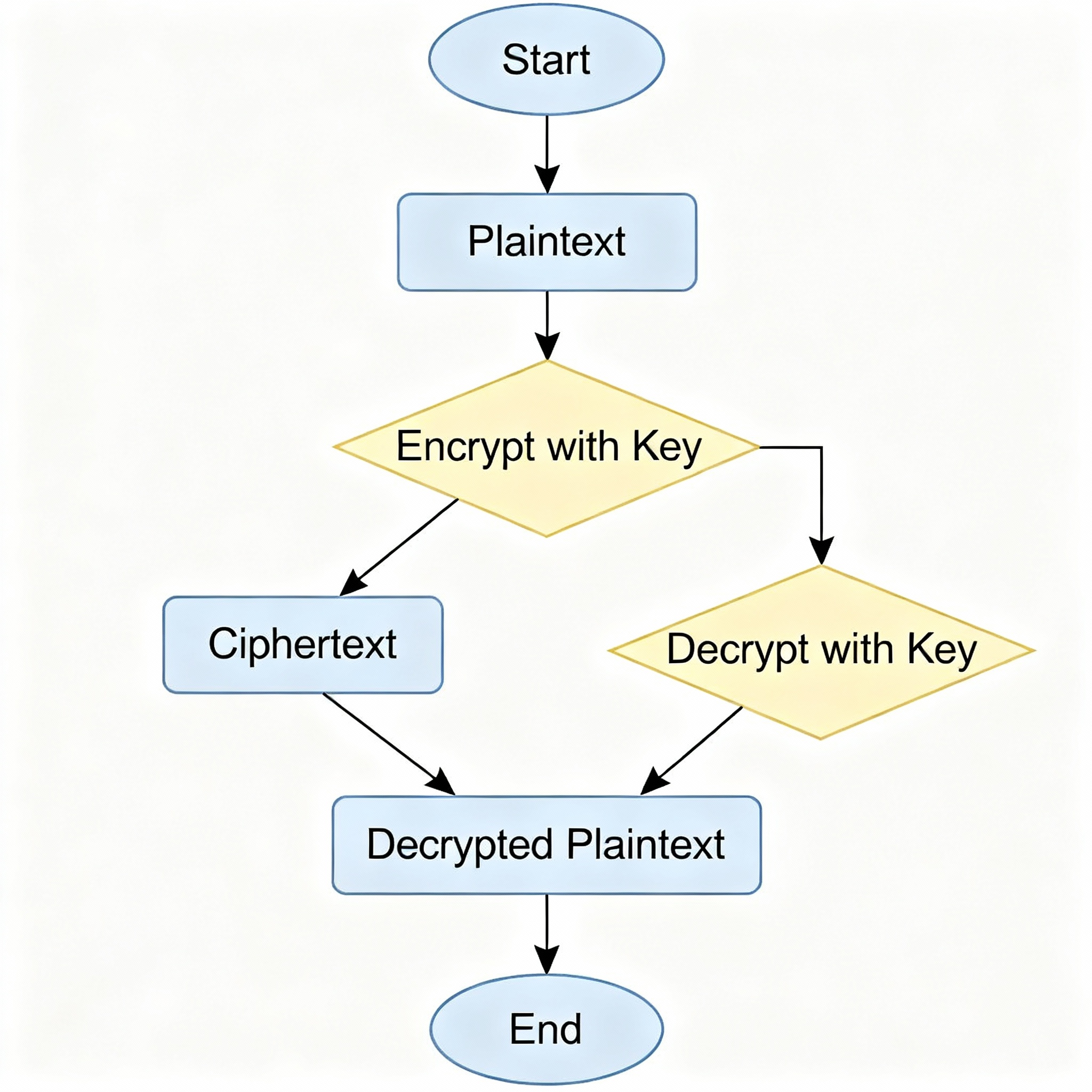
To understand what is data encryption, it helps to look at how it actually functions behind the scenes. When data is transmitted across the internet, it doesn’t travel directly from one device to another. It passes through numerous routers, servers, and networks — many of which are public and therefore vulnerable. Encryption ensures that even if this data is intercepted, it cannot be read or modified.
Here’s how it works in practice:
- Encryption Phase: The sender uses an encryption algorithm and a cryptographic key to transform plaintext into ciphertext. This ciphertext appears as a random string of numbers and letters that makes no sense to anyone without the correct key.
- Transmission: The encrypted data travels across the network. Even if intercepted, it remains incomprehensible.
- Decryption Phase: The recipient uses a decryption key — often mathematically related to the encryption key — to convert the ciphertext back into readable data.
The strength of encryption depends on the complexity of the algorithm and the length of the key. Longer, more complex keys are harder to crack through brute-force attacks.
This process is conceptually similar to how digital currencies like Bitcoin protect transaction information. While cryptocurrency uses blockchain and cryptographic hashing to secure financial exchanges, encryption uses mathematical algorithms to protect private data in motion or at rest. Understanding both helps explain cryptocurrency principles as part of a larger conversation about digital security and privacy.
Types of Encryption Methods: Symmetric and Asymmetric
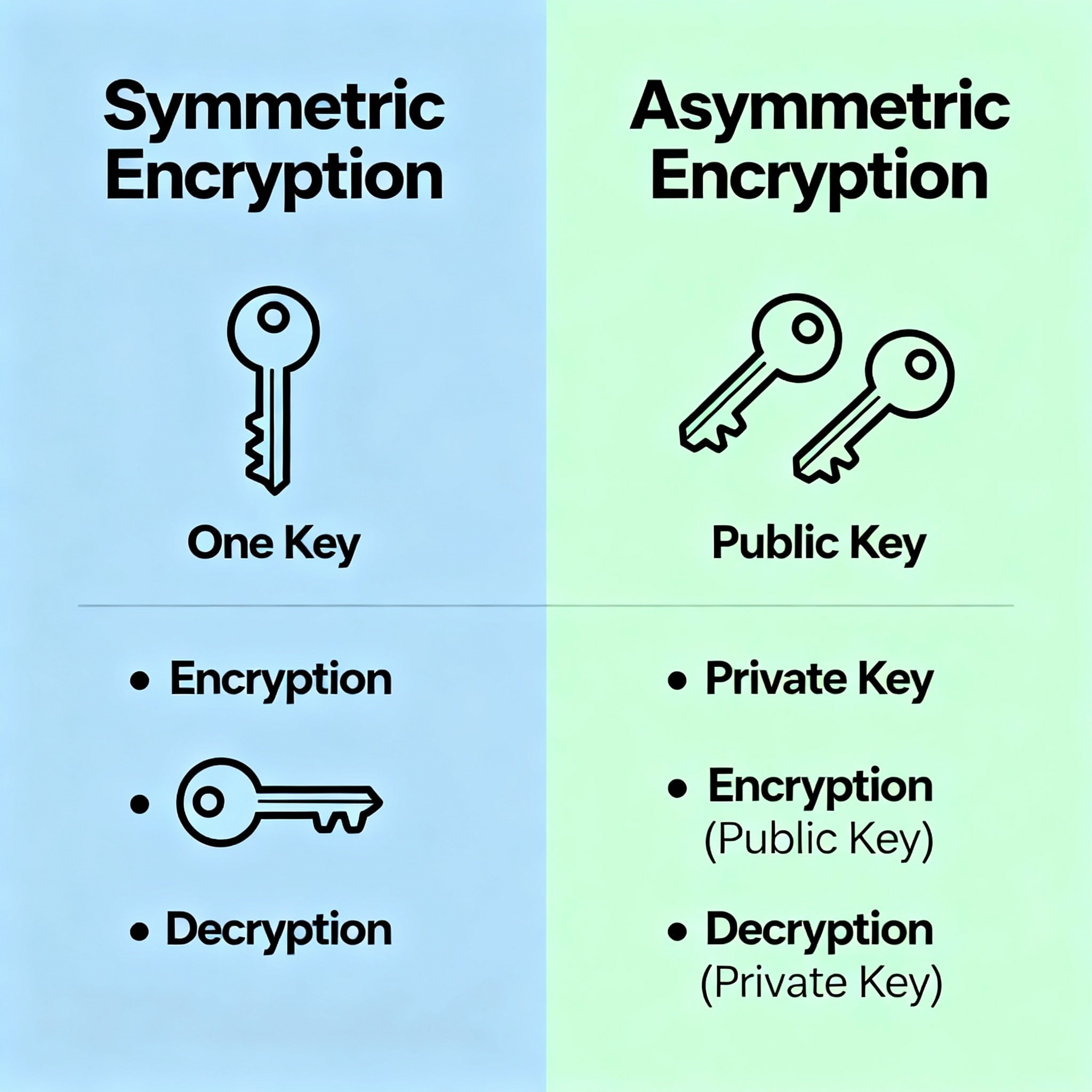
Encryption techniques can be categorized into two primary types — symmetric and asymmetric — based on how keys are used for encryption and decryption.
Symmetric Encryption
Symmetric encryption, also known as private-key encryption, uses the same key for both encryption and decryption. This means that the sender and receiver must both have access to the same key.
The main advantage of symmetric encryption is speed. It is faster than asymmetric encryption, making it suitable for encrypting large volumes of data such as databases or entire drives. However, it comes with one key challenge: securely sharing the encryption key between parties. If a hacker intercepts the key, they can decrypt all the data.
Common symmetric encryption algorithms include:
- AES (Advanced Encryption Standard)
- DES (Data Encryption Standard)
- 3DES (Triple Data Encryption Standard)
Asymmetric Encryption
Asymmetric encryption, or public-key encryption, uses two separate but related keys: a public key for encryption and a private key for decryption. The public key can be shared freely, while the private key must remain secret.
This type of encryption is commonly used for secure communications such as email encryption, digital signatures, and website SSL/TLS certificates. It ensures that even if the public key is known, only the holder of the private key can decrypt the data.
Common asymmetric algorithms include RSA (Rivest–Shamir–Adleman) and DSA (Digital Signature Algorithm).
Just like whats crypto uses public and private keys to manage secure transactions in blockchain systems, asymmetric encryption relies on similar key-based cryptography to safeguard digital communication.
Common Encryption Algorithms
Several algorithms form the backbone of encryption technology today. Each has its strengths, weaknesses, and specific use cases.
- DES (Data Encryption Standard): An early encryption standard that is now considered outdated due to its short key length, making it vulnerable to brute-force attacks.
- 3DES (Triple Data Encryption Standard): An improved version of DES that applies the encryption process three times for added security.
- AES (Advanced Encryption Standard): The most widely used modern symmetric encryption algorithm, known for its speed and strength. It is used in applications like secure messaging, file compression tools, and encrypted storage.
- RSA (Rivest–Shamir–Adleman): A leading asymmetric encryption algorithm that enables secure data transmission and digital signatures.
- Twofish: A high-speed, flexible symmetric algorithm often used in both software and hardware encryption.
- RC4: A stream cipher previously used in wireless encryption protocols (WEP and WPA), though now considered insecure.
These algorithms form the technical foundation of modern encryption — much like blockchain algorithms underpin cryptocurrency concepts and digital transaction integrity.
Encryption in Transit vs. Encryption at Rest
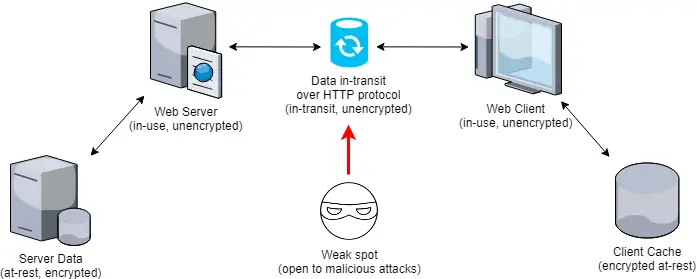
Data can exist in two states — in transit and at rest — and encryption is applied differently in each scenario.
Data in Transit
Data is in transit when it is being transferred across networks, such as when sending an email or conducting an online transaction. Because it passes through multiple points, it is highly vulnerable to interception. Encrypting data during transmission ensures that even if it is intercepted, it cannot be read.
End-to-end encryption (E2EE) is a method where only the sender and recipient have the keys needed to decrypt the data. Messaging applications like WhatsApp and Signal use this technology, ensuring that not even the service providers can access user messages.
Data at Rest
Data at rest refers to information stored on physical or cloud-based storage devices. Examples include files on a hard drive, documents in a database, or backups in the cloud. While less exposed than data in transit, stored data is still vulnerable to theft, especially in the case of device loss or unauthorized access.
Technologies like Transparent Data Encryption (TDE) are used by major database systems to encrypt data stored on disks and backups automatically.
Both types of encryption ensure comprehensive protection — safeguarding information whether it’s being transmitted or stored.
End-to-End Encryption Explained
End-to-end encryption is one of the most secure forms of data protection. In this method, the encryption and decryption happen only on the devices of the sender and receiver. This means that even service providers who transmit the data cannot read or alter it.
Applications such as WhatsApp, Telegram, and Signal employ end-to-end encryption to protect conversations and file exchanges. It ensures complete privacy and prevents third-party interception.
This concept is somewhat parallel to blockchain’s approach to privacy in cryptocurrency concepts, where transactions are verified and secured cryptographically without intermediaries.
Also Read: What is Cryptocurrency and How Does It Work?
Benefits of Data Encryption
Encryption is indispensable for safeguarding data and ensuring trust in digital communication. Its key benefits include:
- Data Integrity: Encryption helps detect and prevent tampering. Any modification to encrypted data becomes immediately apparent when decrypted.
- Regulatory Compliance: Many industries, such as healthcare and finance, require encryption to comply with privacy regulations like GDPR and HIPAA.
- Multi-Device Security: Encryption protects data across different devices, from smartphones to servers.
- Cloud Security: Encryption secures data during upload and storage in the cloud, ensuring privacy even if the cloud provider is compromised.
- Protection for Remote Offices: With many employees working remotely, encryption ensures secure access to company systems from different locations.
- Intellectual Property Protection: Digital rights management systems rely on encryption to prevent unauthorized copying and use of copyrighted material.
Much like how what is crypto relies on encryption to safeguard digital financial assets, traditional data encryption ensures the protection of all forms of digital information.
Real-World Applications of Encryption
Encryption plays a central role in nearly every aspect of modern digital life. Common applications include:
- Online Banking and E-commerce: Encryption secures payment data and transactions.
- Secure Websites: Websites using HTTPS encrypt all data exchanged between browsers and servers.
- Messaging Services: Apps like WhatsApp, Telegram, and iMessage use encryption to protect messages.
- Cloud Storage: Files stored in Google Drive, Dropbox, or OneDrive are encrypted to prevent unauthorized access.
- Email Communication: Protocols like OpenPGP and S/MIME encrypt emails to ensure confidentiality.
- VPN Services: Virtual Private Networks encrypt internet traffic, hiding user activity from trackers and hackers.
- Device Security: Modern smartphones and computers use full-disk encryption to protect stored data.
Just as encryption ensures financial security in crypto currency meaning, these applications ensure privacy and data protection in our daily interactions online.
Limitations and Challenges of Encryption
Despite its many advantages, encryption is not a complete cybersecurity solution. It comes with certain limitations:
- Key Management: Losing the encryption key means permanent loss of access to the data.
- Performance Impact: Encrypting large datasets can consume system resources and slow performance.
- User Responsibility: Weak passwords or poor configurations can undermine even the strongest encryption.
- Legal Restrictions: Some countries regulate or restrict certain encryption technologies.
Still, when combined with strong passwords, updated systems, and other security measures, encryption remains one of the most powerful tools against data breaches and cyber threats.
Conclusion
In a world increasingly driven by data, understanding what is data encryption is essential for ensuring digital security. Encryption transforms sensitive information into a secure, unreadable form that protects it from hackers, identity thieves, and corporate espionage.
From online shopping and email communication to cryptocurrency concepts and cloud computing, encryption forms the backbone of digital trust. It ensures that information remains private, authentic, and intact, whether stored on a device or transmitted across the internet.
Just as whats crypto uses encryption to create a secure and transparent financial ecosystem, encryption in cybersecurity safeguards the integrity and confidentiality of data everywhere. In short, encryption is not just a technical tool — it is a fundamental principle that keeps the modern digital world safe, connected, and trustworthy.




