Steganography is one of the oldest and most fascinating techniques used to hide information. It blends the ideas of secrecy, creativity, and technology in a way that makes communication invisible rather than simply unreadable. While it originated thousands of years ago, steganography has become highly relevant to today’s digital world, especially as cyber threats grow more sophisticated and threat actors look for new ways to evade detection.
Understanding what is steganography, how it works, and why it matters in modern cybersecurity allows individuals, businesses, and digital users to stay more aware and better protected.
Steganography meaning “covered writing,” is the practice of hiding information inside another medium. Unlike encryption, which transforms data into unreadable ciphertext, steganography conceals the very existence of the information. Files such as images, videos, audio clips, documents and even network traffic can secretly carry hidden messages without appearing unusual to the naked eye.
For centuries, societies used steganography to send secret messages. Today, it has evolved into a digital technique used for both legitimate purposes and malicious intent. The rising use of steganography in cyber security explains why understanding this concept is more important than ever.
What Is Steganography?

Steganography is the art and science of concealing data inside another file or object so that no one suspects hidden communication is taking place. It can hide text, images, audio, video, executable files, or sensitive data within other seemingly harmless files.
The term is derived from two Greek words:
“Steganos” meaning hidden or covered, and
“Graphein” meaning writing.
In essence, steganography disguises a secret message by embedding it within another digital or physical medium. Unlike encryption, steganography does not scramble the message; instead, it hides it so effectively that observers do not realize anything unusual exists.
Historically, this practice has taken many forms:
- Ancient Greeks carving messages onto wooden tablets and covering them with wax.
- Romans writing invisible ink messages only visible under heat or light.
- Spies embedding secret codes between lines of ordinary letters.
The evolution from physical to digital steganography happened naturally as technology advanced. Today, cybercriminals and hackers also use it to conceal malicious payloads or hide stolen data inside benign-looking files.
How Steganography Works
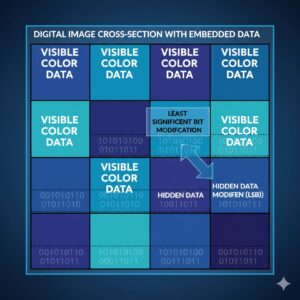
To understand steganography fully, it helps to look at the mechanics behind how data is hidden. The goal is always the same: embed information in a way that appears natural and raises no suspicion.
Least Significant Bit (LSB) Technique
One of the most popular digital techniques is the Least Significant Bit method. Every image, audio, or video file is composed of binary data. Modifying the final bit (the “least significant” one in each byte) does not meaningfully affect how the file looks or sounds, but it opens subtle storage space for hidden data.
For example, in a digital image:
- Each pixel stores color using multiple bytes.
- Changing the last bit of each byte allows hidden data to be inserted.
- Millions of pixels mean millions of opportunities to embed information.
A viewer sees the same image, but a decoder can extract the hidden message.
Text-Based Concealment
Another method involves embedding information inside written text:
- Using patterns in spacing.
- Replacing specific letters.
- Positioning secret words at defined intervals.
While simple, this method can look unnatural if not done carefully.
Embedding Data in Metadata and File Headers
Many digital files include metadata—information about the file that most users never access. Attackers and covert communicators take advantage of unused or overlooked sections of metadata by inserting secret information.
Concealing Data in Network Protocols
Network steganography hides information within:
- TCP, UDP, or ICMP packets
- Packet timing patterns
- Protocol headers
This method is harder to detect because the data moves across networks disguised as routine traffic.
Types of Steganography
Digital steganography can be categorized into five major types. Each type differs in method, complexity, and detectability.
Text Steganography
This involves hiding information in text files. Techniques include:
- Manipulating letter spacing or alignment
- Substituting words
- Using structured grammar rules to embed data
- Adding invisible characters that contain encoded messages
Although text files are small and offer limited space, they can be used strategically when subtlety is required.
Image Steganography
Images are the most common carriers for hidden messages. They contain millions of pixels and abundant redundant data. Most steganography examples online involve hiding information in:
- JPEG
- PNG
- BMP
- GIF
This method uses techniques like LSB modification, color channel modification, or frequency-domain embedding.
Because images are widely shared on social media and websites, cyber attackers often use them as hidden vectors for malicious code.
Audio Steganography
Audio files contain complex waveforms and high data capacity. Hidden messages can be embedded through:
- LSB changes
- Frequency manipulation
- Altering echo patterns
- Using phase coding
Audio-based steganography is harder to detect but also more complex to create.
Video Steganography
Video files combine both visual and audio streams, making them ideal for concealing large amounts of information.
Two common techniques include:
- Embedding data in raw video before compression
- Embedding data within compressed video streams
Because videos are large, any subtle change goes unnoticed to human observers.
Network Steganography
Also known as protocol steganography, this type hides information within:
- Headers of network packets
- Traffic timing
- Sequence numbers
- Flags in packets
It is particularly sophisticated and used in targeted cyberattacks.
Steganography vs. Cryptography
Though both aim to protect information, steganography and cryptography work differently.
Cryptography turns data into unreadable ciphertext. Anyone can see the encrypted file but cannot understand its content without a key.
Steganography hides the existence of the message itself. The file looks ordinary and does not alert observers that communication is happening.
Both can be combined:
- Data is encrypted.
- Then embedded inside another file using steganography.
This makes detection and decryption significantly harder.
Steganography and NFTs
As the digital art world grows, steganography is beginning to merge with NFTs. Many NFT creators embed hidden content such as:
- Exclusive artwork
- Secret files
- Hidden messages
- High-resolution images
- Access codes
Private metadata stored within NFTs can act as a steganographic container. This trend is growing across industries such as:
- Gaming
- Ticketing
- Digital memberships
- Intellectual property
The use of steganography in NFTs allows creators to offer hidden value accessible only to token holders.
Also Read: What is the Internet of Things?
Legitimate Uses of Steganography
Steganography isn’t always malicious. It has several beneficial applications.
Avoiding Censorship
Activists or journalists hide messages inside images or documents to bypass oppressive censorship systems.
Digital Watermarking
Used for:
- Copyright protection
- Authenticity validation
- Preventing unauthorized duplication
Watermarks are invisible but traceable.
Secure Communication
Government agencies, law enforcement, and intelligence units use steganography to exchange sensitive data covertly.
How Steganography Is Used in Cyber Attacks
Despite its legitimate uses, steganography has gained attention due to its role in cybercrime.
Hiding Malicious Payloads
Attackers embed malware inside:
- Images
- Videos
- Documents
- Audio files
When opened, these files execute hidden commands.
Ransomware and Data Exfiltration
Hackers conceal:
- Encryption keys
- Stolen data
- Attack instructions
These can be hidden in seemingly harmless media files and transmitted without detection.
Embedding Commands in Web Pages
Attackers use HTML whitespace or hidden script comments to deliver malicious instructions to infected devices.
Malvertising Campaigns
Banner ads contain malicious scripts hidden through steganography that activate when viewed.
Real-World Steganography Attacks
E-commerce Skimming Campaign (2020)
Hackers hid skimming malware inside SVG logos on checkout pages. Since SVG files looked legitimate, they bypassed scanners.
SolarWinds Supply Chain Incident
Attackers used steganography to disguise malicious command-and-control messages inside XML files during the widespread breach.
Industrial Enterprise Attacks
Hackers used images hosted on legitimate platforms like Imgur to deliver malware hidden inside Excel documents via steganographic payloads.
Detecting Steganography (Steganalysis)
Detection is difficult because the files look ordinary. Analysts use:
- Hex editors to detect anomalies
- StegExpose, StegAlyze, and other tools
- Advanced algorithms to detect unusual patterns
However, identifying steganography among millions of online files remains a major challenge.
How to Mitigate Steganography-Based Attacks
Awareness and Training
Employees must be trained to:
- Avoid downloading media from unknown sources
- Recognize suspicious attachments
- Understand that even harmless-looking files can be dangerous
Web Filtering and Patch Management
Restricting access to unsafe sites and applying timely updates helps reduce exposure to embedded threats.
Endpoint Monitoring
Behavioral monitoring helps detect unusual file activity, such as hidden scripts executing inside a media file.
Threat Intelligence
Organizations should monitor global threat trends, including attacks involving steganography.
Multi-Layered Security
A combination of:
- Firewalls
- Endpoint protection
- Network monitoring
reduces the risk of attacks that rely on concealed data.
Conclusion
Steganography has traveled centuries from carved messages hidden beneath wax to invisible digital communication embedded inside images, videos, and network protocols. Understanding what is steganography, its history, methods, and risks helps organizations and individuals appreciate both its power and its dangers.
In modern cybersecurity, steganography serves a dual role. It is a creative tool used to protect intellectual property, bypass censorship, and support secure communication. At the same time, it is a powerful weapon used by cybercriminals to deliver attacks, hide malicious payloads, and exfiltrate sensitive data without detection.
As digital communication grows more complex, the need for awareness, detection, and security around hidden information becomes increasingly essential. Steganography may be hidden by design, but understanding it brings clarity and protection to an ever-evolving digital world.




