Security needs have changed significantly in recent years. Traditional access control methods like keys, cards, and PINs are increasingly vulnerable to loss, theft, and misuse. As organizations grow and security risks increase, businesses are looking for smarter and more reliable ways to manage access to their premises. Facial recognition access control systems have emerged as a modern solution that combines convenience, speed, and enhanced security. This guide helps decision-makers understand how these systems work and how to choose the most suitable option based on real operational needs.
What Is a Facial Recognition Access Control System?
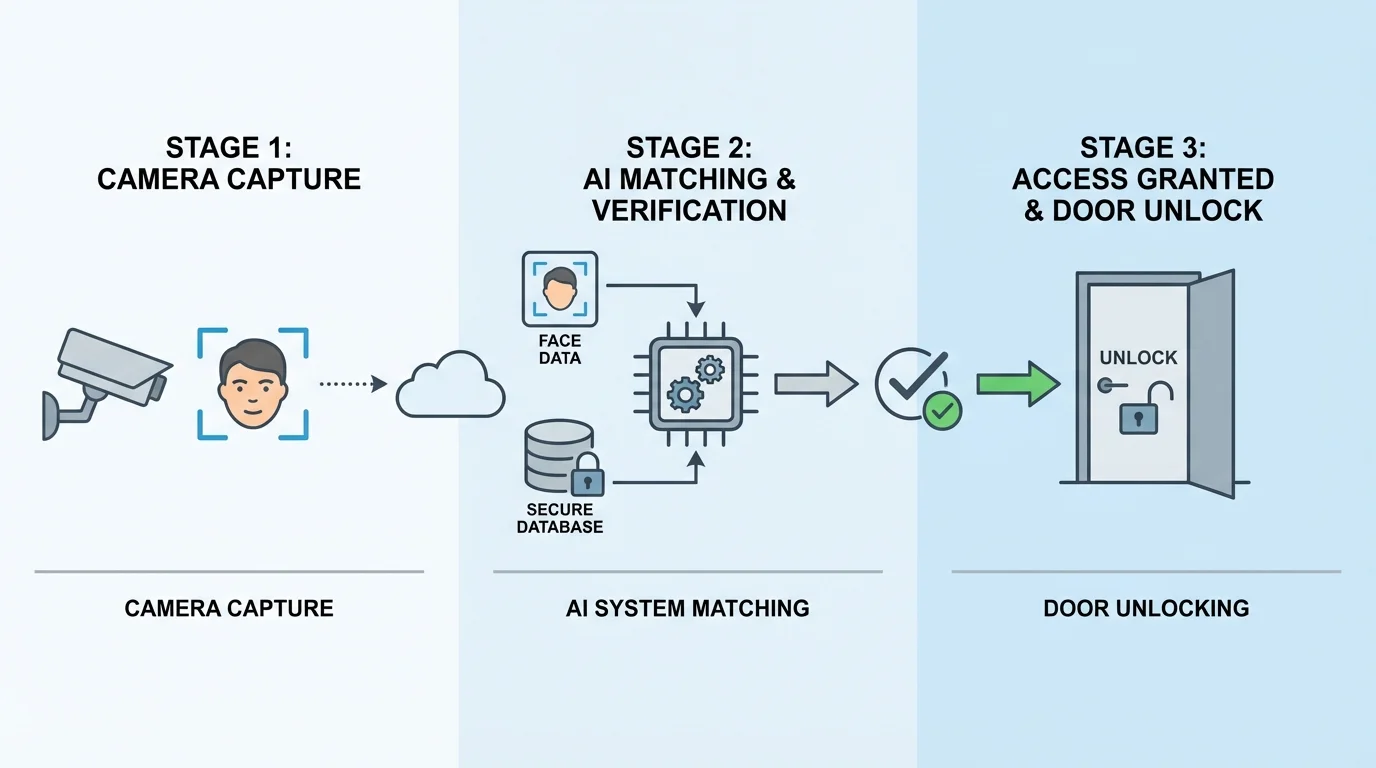
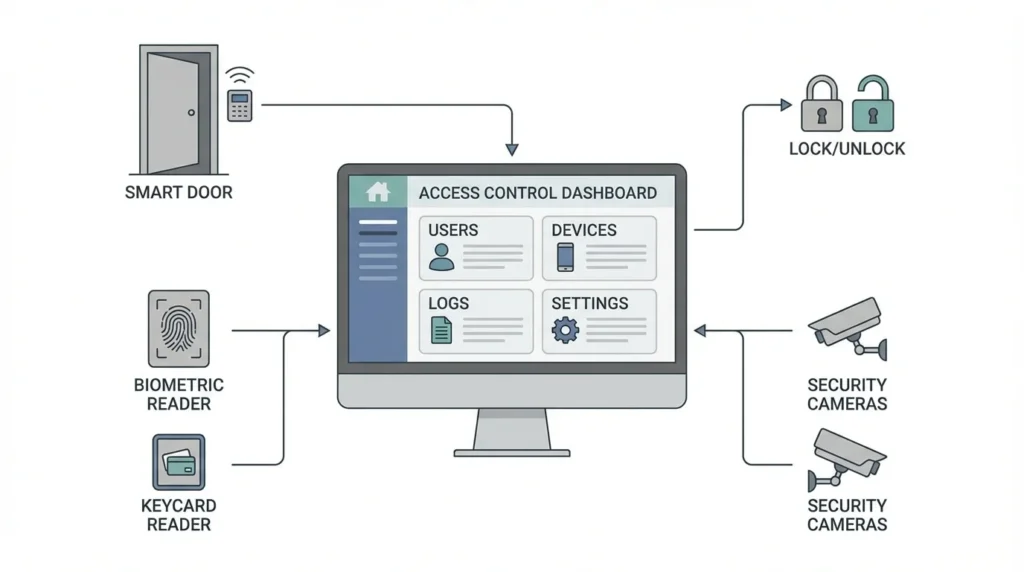
A facial recognition access control system is a security solution that verifies a person’s identity by analyzing unique facial features before granting access to a restricted area. It uses cameras and artificial intelligence algorithms to match a live facial image with stored face data.
Key elements of a typical system include
- A camera that captures facial images
- Facial recognition software that analyzes and matches faces
- A database that securely stores enrolled facial data
- An access control mechanism such as a door lock or turnstile
Unlike cards or passwords, facial recognition relies on biometric traits that are difficult to duplicate, making it a more secure and user-friendly option.
Why Businesses Are Switching to Facial Recognition Access Control
Many organizations are moving away from traditional access methods because they require manual management and are prone to security gaps. Facial recognition systems offer a more automated and reliable alternative.
The main reasons businesses are adopting these systems include
- Contactless access, which reduces physical contact and improves hygiene
- Improved security by preventing unauthorized access using stolen credentials
- Faster entry processes, especially in high-traffic areas
- Reduced administrative effort related to card issuance and replacement
- Better scalability for organizations with growing teams
Key Factors to Consider When Choosing a Facial Recognition Access Control System
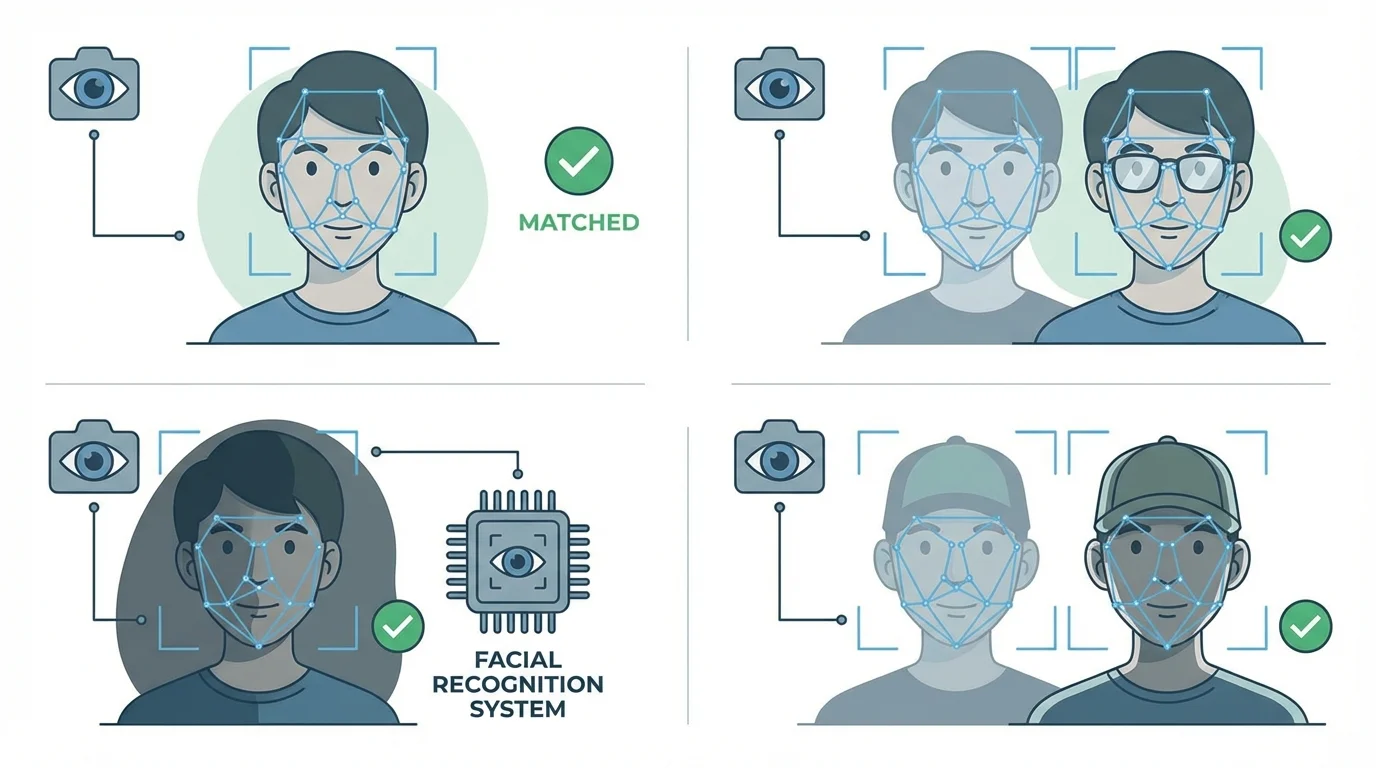
Accuracy and Recognition Performance
Accuracy is one of the most critical aspects of any facial recognition system. A system must correctly identify authorized individuals while rejecting unauthorized ones.
Important accuracy considerations include
- The system’s ability to minimize false acceptances and false rejections
- Consistent performance under different lighting conditions
- Reliable recognition even when users wear glasses, masks, or have minor facial changes
Speed and Response Time
Speed directly affects user experience and operational efficiency. Slow systems can cause delays and congestion at entry points.
Key points to evaluate are
- Real-time recognition capability
- Processing speed during peak entry hours
- Stability of performance when multiple users access simultaneously
Camera Quality and Hardware Specifications
The quality of the camera significantly impacts recognition accuracy. Poor hardware can reduce system effectiveness even if the software is advanced.
Hardware-related factors include
- Camera resolution and image clarity
- Suitability for indoor or outdoor environments
- Support for low-light or infrared imaging
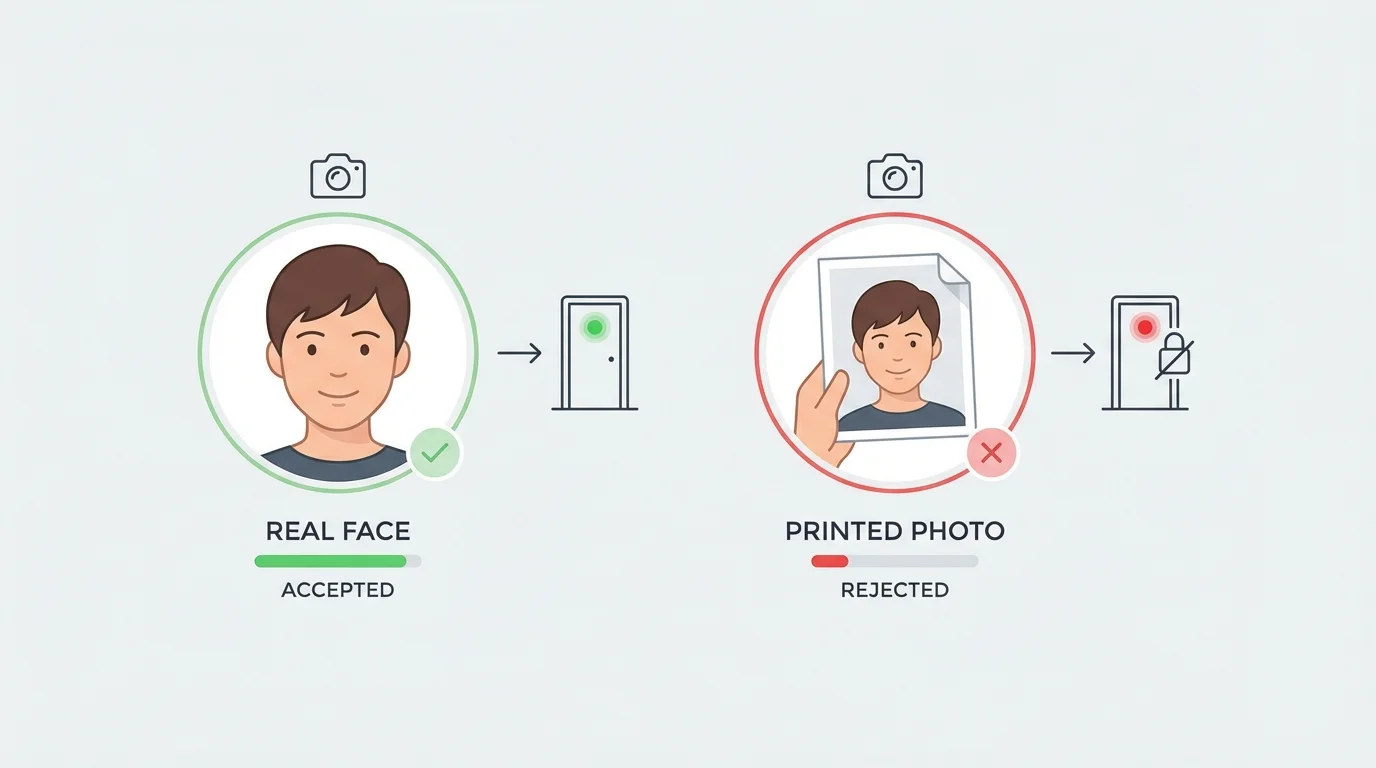
Anti-Spoofing and Liveness Detection
Anti-spoofing features protect the system from attempts to gain access using photos, videos, or masks.
Essential anti-spoofing capabilities include
- Detection of live facial movements
- Resistance to printed or digital image attacks
- Advanced liveness detection using depth or motion analysis
System Scalability
A facial recognition system should support future growth without requiring a complete replacement.
Scalability considerations include
- Maximum number of users the system can store
- Support for multiple doors and locations
- Ease of adding new users and access points
Integration Capabilities
Integration ensures that the access control system works seamlessly with other security and business tools.
Common integration needs include
- Compatibility with existing access control hardware
- Integration with attendance, HR, or payroll systems
- Support for CCTV monitoring and visitor management software
Data Security and Privacy Compliance
Facial data is sensitive and must be protected properly. A reliable system prioritizes data security and privacy.
Key privacy and security aspects include
- Encryption of facial data during storage and transmission
- Controlled access to biometric data
- Clear data retention and deletion policies
Cloud-Based vs On-Premise Facial Recognition Systems
Facial recognition systems can be deployed either through cloud-based platforms or on local servers.
Cloud-based systems typically offer
- Easier scalability and remote management
- Lower upfront infrastructure costs
- Dependence on stable internet connectivity
On-premise systems generally provide
- Greater control over data storage
- Reduced reliance on external networks
- Higher initial setup and maintenance costs
The right choice depends on organizational size, data sensitivity, and IT capabilities.
Industry-Specific Requirements to Evaluate
Corporate Offices
Corporate environments require systems that balance security with employee convenience.
Common requirements include
- Seamless employee entry and exit tracking
- Controlled access to restricted departments
- Efficient visitor and contractor management
Manufacturing and Industrial Facilities
Industrial sites often operate in challenging conditions and require durable systems.
Key considerations include
- Reliable recognition during shift changes
- Hardware suitable for dusty or low-light environments
- Integration with workforce attendance systems
Healthcare Facilities
Healthcare settings prioritize hygiene and strict access control.
Important needs include
- Contactless access to reduce infection risk
- Controlled entry to sensitive areas
- Compliance with data protection requirements
Educational Institutions
Schools and colleges require scalable systems for large user groups.
Typical requirements include
- Campus-wide access management
- Separate access rules for students, staff, and visitors
- Simple enrollment and administration
Residential and Gated Communities
Residential environments focus on safety and convenience for residents.
Common features include
- Secure resident access
- Temporary access for guests
- Remote monitoring and management
User Experience and Ease of Use
A system may be technically advanced, but poor usability can reduce adoption and effectiveness.
User experience factors include
- Simple and quick face enrollment process
- Easy-to-use admin dashboard
- Clear access logs and reporting features
Installation, Maintenance, and Support
Installation and ongoing support play a major role in long-term system performance.
Important points to assess include
- Complexity of installation and setup
- Frequency of software updates
- Availability of technical support and maintenance services
Cost Considerations and ROI
Cost evaluation should go beyond the initial purchase price.
Key cost-related factors include
- Hardware and software licensing fees
- Installation and maintenance expenses
- Long-term savings from reduced manual management and improved security
A well-chosen system often delivers strong return on investment through operational efficiency and risk reduction.
Questions to Ask Vendors Before Finalizing a System
Asking the right questions helps ensure the system meets real requirements.
Important questions include
- What accuracy levels does the system consistently achieve
- How is facial data stored and protected
- What upgrade and expansion options are available
- What level of technical support is provided
Conclusion
Choosing the ideal facial recognition access control system requires careful evaluation of accuracy, security, usability, and long-term suitability. Businesses must align technology choices with their operational needs, industry requirements, and privacy responsibilities. A well-selected system not only strengthens security but also improves efficiency and user experience, making it a valuable long-term investment.