In today’s digital-first world, data is one of our most valuable assets. Every login, online purchase, medical record, business document, financial transaction, or private conversation leaves behind sensitive information that must be protected. When this information falls into the wrong hands, the consequences can be costly, disruptive, and long-lasting. This is why understanding data breaches — and how to prevent them — is essential for individuals, businesses, and governments alike.
This detailed guide explores what a data breach is, how data leaks happen, the risks involved, and practical prevention strategies to help safeguard personal and organizational data.
What is a Data Breach?
A data breach is an incident in which unauthorized individuals gain access to confidential, protected, or sensitive information. This information can be viewed, stolen, shared, or used illegally without the owner’s consent.
People often assume only major corporations or government agencies are targeted. In reality, anyone with personal data stored on a device or online account is vulnerable — including everyday users at home.
Sensitive data commonly exposed in breaches may include:
- Full names and home addresses
- Email addresses and phone numbers
- Bank account and credit card details
- Login credentials and passwords
- Health records or government IDs
- Intellectual property and business plans
Once leaked, this information can be sold, exploited for fraud, or used for identity theft.
How Do Data Breaches Happen?
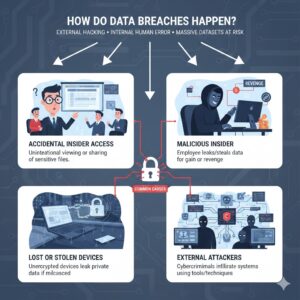
A breach can originate externally through hacking — or internally through human error. Even a small slip-up can expose massive datasets.
Here are the most common causes:
Accidental Insider Access
Someone unintentionally views or shares sensitive files without proper authorization. No harmful intention is required for a breach to occur.
Malicious Insider
An employee or contractor with authorized access intentionally leaks or steals data for personal gain or revenge.
Lost or Stolen Devices
Unencrypted laptops, phones, or external drives containing private data can leak information if misplaced.
External Attackers
Cybercriminals deliberately infiltrate systems to steal valuable information, often using sophisticated tools and techniques.
Methods Hackers Use to Breach Data
Cybercriminals continuously evolve their strategies. Some of the most dangerous attack vectors include:
Phishing
Fraudulent emails or messages trick users into revealing passwords or clicking malware-infected links. These attacks often impersonate trusted brands or coworkers.
Brute Force Attacks
Automated systems repeatedly guess password combinations until they gain access.
Weak passwords make this method extremely effective.
Malware Infections
Malicious software like spyware, trojans, or ransomware can exploit system vulnerabilities to capture, lock, or leak sensitive information.
Also Read:What Is a Replay Attack? A Complete Definition and Explanation
What Information Do Hackers Target?
Attackers primarily seek opportunities for financial gain or data exploitation. They commonly target:
- Personal Identifiable Information (PII) — leading to identity theft or fraud
- Corporate intellectual property — confidential files, patents, contracts
- Credentials used for network access — opening the door to deeper breaches
- Payment card details — stolen via skimmers or compromised websites
- Business communication files — email records, negotiations, and strategy docs
A typical breach may go undetected for months, giving attackers plenty of time to misuse the stolen data.
Real-World Impact of Data Breaches
The damage can be devastating — far beyond temporary disruptions.
Impact on Businesses
- Financial loss due to lawsuits, fines, and recovery costs
- Permanent reputation damage and customer distrust
- Business operations and supply chain interruptions
Major cases like Yahoo, Equifax, and Marriott show how deeply a breach can affect global brands.
Impact on Governments
- Exposure of national intelligence and classified information
- Threats to critical infrastructure and citizen safety
Impact on Individuals
- Identity theft and financial theft
- Long-term credit damage
- Emotional distress and loss of privacy
Hackers may impersonate victims online for years after a breach occurs.
How to Detect If Your Data Was Exposed
If credentials are leaked, criminals often sell information on the dark web. Signs your data may be compromised include:
- Unexpected password resets or blocked accounts
- Unauthorized transactions or banking alerts
- Passwords no longer working
- Communications from unfamiliar sources
- Sudden increase in spam messages
- Login notifications from unknown locations
Users can also check breach-monitoring tools online to verify whether their emails or accounts were exposed previously.
How to Prevent Data Breaches
Preventing a breach requires both secure technology and responsible user behavior. Here are essential protection strategies:
Adopt Strong Cybersecurity Measures
- Use reputable antivirus and firewall tools to detect threats such as malware and phishing.
- Enable automatic scanning for harmful links, downloads, and network intrusions.
Use Strong, Unique Passwords
- Avoid common or reused passwords.
- Consider a secure password manager to store and create long, complex passwords.
Activate Multi-Factor Authentication (MFA)
Requiring additional identity verification makes unauthorized access significantly harder.
Update Devices and Software Regularly
Updates patch security flaws that attackers may otherwise exploit.
Encrypt Sensitive Data
Encryption ensures stolen files remain unreadable without authorization.
Be Cautious With Public Wi-Fi
Avoid accessing financial or sensitive accounts on open networks unless using a secure VPN for encryption.
Stay Aware of Phishing Techniques
- Verify sender identities
- Check URLs before clicking links
- Never share confidential information by email
Implement Strong Corporate Security Policies
For organizations:
- Mandate BYOD security rules
- Limit third-party system access
- Train employees to recognize social engineering
- Monitor network behavior for anomalies
Security is only as strong as the weakest point — often a single user.
FAQs
What should I do first if I become a victim of a data breach?
- Change passwords immediately
- Notify banks or financial providers
- Freeze credit reports if identity theft is suspected
- Monitor accounts for unusual activity
Can small businesses be targeted too?
Yes, cybercriminals often target smaller companies due to weaker defenses.
How long can a breach affect someone?
Years — stolen data can circulate across hacker forums indefinitely.
Can a data breach happen offline?
Yes. Physical device theft or unauthorized access to printed documents can also leak sensitive information.
Conclusion
Data breaches are now a constant threat in our connected lives. With every online action producing digital traces, privacy becomes more vulnerable if proper protections are not in place. But with the right mix of cybersecurity tools, strong password habits, encryption, and constant vigilance, both individuals and organizations can significantly reduce the risk of exposing sensitive information.
Taking security seriously is not optional anymore — it is a crucial responsibility in the modern digital world.





