Cyberattacks have evolved significantly over the years, but some older attack techniques remain relevant because of legacy systems, unpatched software, and poor network hygiene. One such threat is the teardrop attack, a classic yet dangerous form of denial-of-service assault that can still disrupt systems if proper defenses are not in place. Understanding what a teardrop attack is, how it works, and how to prevent it is essential for organizations and individuals who want to maintain strong cybersecurity defenses.
This guide explains the teardrop cyber attack in depth, explores how it differs from other denial-of-service attacks, highlights real-world examples, and provides practical prevention strategies to minimize risk.
What Is a Teardrop Attack

To understand what is a teardrop attack, it helps to first understand how data normally travels across networks.
A teardrop attack is a type of denial-of-service attack that exploits vulnerabilities in the way operating systems reassemble fragmented data packets. In normal network communication, large data packets are split into smaller fragments so they can travel efficiently across networks. Once they reach their destination, the system reassembles them in the correct order.
In a teardrop attack, an attacker deliberately sends malformed or overlapping packet fragments. These corrupted fragments contain incorrect information in the fragment offset fields, which confuses the receiving system. When the system attempts to reassemble the packets, it fails, leading to system overload, crashes, or complete shutdowns.
Because of this behavior, teardrop attacks are sometimes classified as teardrop DDoS or teardrop DDoS attack methods when used at scale across multiple sources.
Why Teardrop Attacks Are Still a Threat
Many people assume teardrop attacks are outdated because they first gained notoriety in the late nineteen nineties. However, the threat has not disappeared. The primary reason teardrop cyber attacks still matter today is the continued use of outdated or unpatched systems.
Organizations running legacy operating systems, older network hardware, or unsupported applications remain vulnerable. This is particularly common in sectors such as healthcare, local government, manufacturing, and small financial institutions where upgrading systems may be slow or costly.
Even a single vulnerable system can be enough for attackers to cause service disruption, making teardrop attacks relevant in modern cybersecurity discussions.
How Teardrop Attacks Work
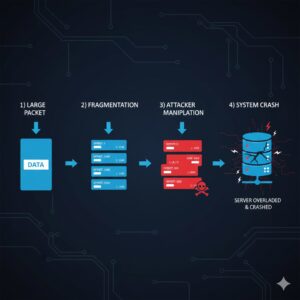
To explain how a teardrop attack works, it is important to understand packet fragmentation.
Normal Packet Fragmentation
When data travels over the internet, it is broken into smaller packets. Each packet contains a fragment offset value that tells the receiving system how to reassemble the data in the correct order. This process usually happens seamlessly and without issue.
Malicious Packet Manipulation
During a teardrop attack, attackers intentionally manipulate the fragment offset fields. They send packets that overlap, contain incorrect offset values, or appear incomplete. When the target system tries to reassemble these packets, it encounters errors it cannot resolve.
Instead of rejecting the packets safely, vulnerable systems attempt to process them repeatedly, consuming memory and processing power. Eventually, the system becomes unstable and crashes.
System Overload and Failure
Because the receiving system cannot properly reassemble the packets, it enters a failure loop. This leads to system freezes, network outages, or complete denial of service. In a teardrop DDoS attack, attackers may send massive volumes of these malformed packets simultaneously, amplifying the impact.
Difference Between Teardrop Attacks and Other DoS Attacks

While teardrop attacks fall under the broader denial-of-service category, they differ from many other attacks in key ways.
Traditional flooding attacks overwhelm a system with massive traffic volume. Teardrop attacks, by contrast, rely on malformed data rather than sheer quantity. Even a relatively small number of corrupted packets can crash a vulnerable system.
This makes teardrop cyber attacks harder to detect because the traffic volume may appear normal at first glance. The damage comes from packet structure rather than traffic size.
History and Origin of Teardrop Attacks
Teardrop attacks first became widely known in the late nineteen nineties. At the time, operating systems such as early Windows and Linux distributions were not equipped to safely handle malformed packet fragments.
Attackers quickly discovered that sending overlapping packet fragments could reliably crash systems. This led to widespread exploitation until vendors released security patches to address the vulnerabilities.
Despite these fixes, the attack remains effective against systems that never received updates or continue to operate on unsupported platforms.
Real-World Examples of Teardrop Attacks
Over the years, several notable cases have demonstrated the impact of teardrop attacks.
Older versions of Windows were especially vulnerable, experiencing frequent crashes when targeted with malformed packet fragments. Legacy Linux systems were also affected before kernel updates addressed the issue.
More recently, similar packet fragmentation concepts have appeared in attacks targeting mobile devices and embedded systems. While not always labeled as teardrop attacks, they use comparable techniques to disrupt system memory handling.
These examples show that while technology evolves, fundamental weaknesses in packet processing can still be exploited.
Industries Most at Risk
Certain industries face a higher risk of teardrop cyber attacks due to reliance on outdated infrastructure.
Healthcare organizations often use legacy medical devices that cannot be easily updated. Local governments may operate older systems due to budget constraints. Small banks and financial institutions sometimes depend on mission-critical applications that are no longer supported.
In these environments, a successful teardrop attack can lead to operational downtime, loss of access to critical data, and reputational damage.
Signs of a Teardrop Attack
Recognizing a teardrop attack can be challenging, but there are common indicators to watch for.
Systems may crash unexpectedly without warning. Networks may become unresponsive even though traffic levels appear normal. Servers might repeatedly restart or freeze during packet processing.
If these symptoms occur alongside unusual packet fragmentation patterns in network logs, a teardrop attack may be the cause.
Teardrop Attack Prevention Strategies
Preventing teardrop attacks requires a combination of technical controls and proactive maintenance.
Keep Operating Systems Updated
One of the most effective ways to prevent a teardrop attack is to keep operating systems and network software fully updated. Security patches often include fixes for packet handling vulnerabilities that attackers exploit.
Upgrade Legacy Systems
Unsupported systems pose a major risk. Replacing or isolating legacy infrastructure significantly reduces exposure to teardrop DDoS attacks.
Use Firewalls and Packet Filtering
Firewalls capable of inspecting packet structure can identify malformed fragments and block them before they reach critical systems. Properly configured network filters add an essential layer of protection.
Disable Unnecessary Services and Ports
Reducing the attack surface by disabling unused services and network ports helps limit potential entry points for attackers.
Network Monitoring and Traffic Analysis
Continuous monitoring allows administrators to detect unusual packet behavior early. Identifying anomalies in fragment offset values can help stop attacks before systems crash.
Mitigation Steps During an Active Attack
If a teardrop attack is detected, immediate action is required.
Affected systems should be isolated to prevent further disruption. Network administrators should analyze traffic logs to identify the source of malformed packets. Applying emergency patches or filtering rules can help stabilize the environment.
After the incident, a thorough review should be conducted to prevent recurrence.
Why Teardrop Attacks Still Matter Today
Even though teardrop attacks are not as common as other modern threats, they remain dangerous due to their simplicity and effectiveness against unpatched systems. Attackers often combine old techniques with modern tools, making awareness and preparation essential.
Organizations that assume older attacks no longer pose a risk may find themselves vulnerable to unexpected outages.
Conclusion
A teardrop attack is a powerful example of how seemingly simple vulnerabilities can cause major disruptions when left unaddressed. By exploiting weaknesses in packet fragmentation and reassembly, attackers can crash systems and deny service without needing massive traffic volumes.
Understanding what is a teardrop attack, how teardrop DDoS attacks work, and how to prevent them is essential for maintaining resilient networks. Regular updates, strong network controls, and proactive monitoring remain the most effective defenses.
In cybersecurity, even older threats deserve attention. Staying informed and prepared is the key to long-term protection.
FAQs
What is a teardrop attack
A teardrop attack is a denial-of-service attack that sends malformed fragmented packets to a target system, causing it to crash when it fails to reassemble the data correctly.
Is a teardrop attack the same as a teardrop DDoS attack
A teardrop DDoS attack is a large-scale version where multiple sources send malformed packets simultaneously, increasing the impact.
Are modern systems vulnerable to teardrop attacks
Most modern systems are protected, but unpatched or legacy systems remain at risk.
How can I detect a teardrop cyber attack
Unexpected crashes, unresponsive systems, and abnormal packet fragmentation patterns are common indicators.
What is the best way to prevent teardrop attacks
Keeping systems updated, using firewalls, monitoring traffic, and retiring legacy infrastructure are the most effective prevention measures.




