In today’s digital-first world, data has become one of the most valuable assets for individuals, businesses, and organizations. From personal information and financial records to trade secrets and intellectual property, data fuels decision-making, innovation, and growth. However, with this increasing reliance on digital data comes a growing risk: data leakage.
Data leakage incidents are becoming more frequent and more damaging. They often serve as the starting point for larger, more devastating data breaches, leading to financial losses, reputational damage, regulatory penalties, and loss of customer trust. Understanding what data leakage is, how it happens, and how to prevent it is no longer optional—it’s essential.
This in-depth guide explores data leakage, its causes, consequences, and most importantly, how to prevent data breaches through effective data loss prevention strategies.
What Is Data Leakage?
Data leakage, sometimes referred to as data leaking, is the unauthorized exposure of sensitive information to individuals or entities that should not have access to it. This information may belong to a private individual, a business, or an entire organization.
Data leakage can occur in multiple ways:
- Electronically – through emails, cloud platforms, websites, messaging apps, or insecure networks.
- Physically – through lost or stolen laptops, mobile devices, USB drives, external hard disks, or printed documents.
The leaked data can include personal details, login credentials, financial information, company records, or confidential intellectual property.
Why Data Leakage Is So Dangerous
For individuals, data leakage can result in identity theft, financial fraud, and emotional distress. For businesses, the consequences are often far more severe and wide-reaching:
- Loss of customer trust
- Damage to brand reputation
- Financial penalties and legal consequences
- Business disruption and downtime
- Competitive disadvantage
Because of these high stakes, understanding data leakage prevention is critical for both individuals and organizations.
Difference Between Data Leakage and Data Breach
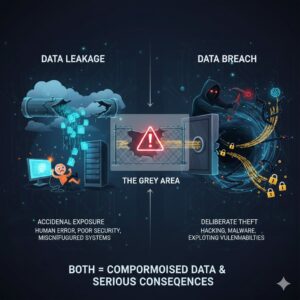
The terms data leak and data breach are often used interchangeably, but there is an important distinction between the two.
What Is a Data Leak?
A data leak typically refers to the accidental or unintentional exposure of sensitive data. It is often caused by:
- Human error
- Poor security practices
- Misconfigured systems
- Insider negligence or misuse
What Is a Data Breach?
A data breach, on the other hand, involves the intentional theft of data by cybercriminals. This usually occurs through:
- Hacking
- Malware attacks
- Exploiting software vulnerabilities
- Credential theft
The Grey Area
In reality, the line between a data leak and a data breach is not always clear. A data leak often becomes the gateway to a data breach. For example, leaked login credentials can allow attackers to access internal systems and steal massive volumes of data.
In short:
- Data leakage is often accidental.
- Data breaches are deliberate attacks.
- Both result in compromised data and serious consequences.
How Does Data Leakage Occur?
Contrary to popular belief, data leakage is not always caused by sophisticated cyberattacks. In many cases, it happens due to human error, negligence, or poor security practices.
Below are the most common ways data leakage occurs:
1. Poor or Outdated Infrastructure
Outdated software, weak system configurations, and improper access permissions can expose sensitive data. Misconfigured cloud storage and unsecured databases are common causes of large-scale data leaks.
2. Social Engineering Attacks
Phishing and spear-phishing attacks trick employees into sharing confidential information or clicking malicious links. These attacks rely on psychological manipulation rather than technical hacking.
3. Weak Password Practices
Reusing passwords, creating weak passwords, or sharing credentials significantly increases the risk of data leakage. Credential stuffing and dictionary attacks exploit these weaknesses.
4. Lost or Stolen Devices
Laptops, smartphones, and tablets often store sensitive data. If these devices are lost or stolen and not properly secured, attackers can easily access the stored information.
5. Software Vulnerabilities
Unpatched software vulnerabilities provide easy entry points for attackers. Failing to apply security updates leaves systems exposed to exploitation.
6. Insider Threats
Disgruntled employees, contractors, or third-party vendors may intentionally leak data. Insider threats are particularly dangerous because insiders often have legitimate access to sensitive systems.
7. Negligence and Human Error
Examples include:
- Sending sensitive data to the wrong email recipient
- Storing confidential files on unsecured USB drives
- Writing down passwords or sensitive information
- Leaving devices unattended in public places
Human error remains one of the leading causes of data leakage worldwide.
What Can Data Leakage Prevention Solutions Protect?
Cybercriminals target data because it can be monetized or exploited in numerous ways. A strong data leakage prevention strategy helps protect various types of sensitive information, including:
1. Personally Identifiable Information (PII)
This includes names, email addresses, phone numbers, dates of birth, government IDs, and credit card details. PII is often used for identity theft and fraud.
2. Customer and Client Data
Databases containing customer records, payment information, order histories, and account details are highly valuable targets.
3. Internal Company Information
This includes internal emails, documents, financial reports, HR records, performance data, and strategic plans.
4. Trade Secrets and Intellectual Property
Confidential designs, formulas, source code, proprietary technology, and business strategies give companies a competitive edge and are prime targets for data theft.
5. Financial Information
Bank statements, tax records, invoices, and financial projections can be exploited for fraud or corporate espionage.
6. Login Credentials
Usernames and passwords allow attackers to take over accounts, access internal systems, and launch further attacks.
Protecting these data types is essential to prevent cascading cybersecurity incidents.
How Is Leaked Data Used by Cybercriminals?
Once attackers obtain leaked data, they can use it for a wide range of malicious activities, making data leakage extremely dangerous.
Common uses include:
- Launching phishing and social engineering attacks
- Committing financial fraud and credit card fraud
- Stealing identities and impersonating victims
- Conducting doxing and harassment campaigns
- Selling stolen data on underground marketplaces
- Extorting individuals or organizations
- Disrupting business operations
- Damaging corporate reputation and customer trust
In many cases, leaked data is sold multiple times, increasing the long-term risk for victims.
Data Loss Prevention for Cybersecurity
Data Loss Prevention (DLP) refers to a set of tools, policies, and practices designed to prevent sensitive data from being exposed, leaked, or stolen.
Effective data loss prevention is not a one-time effort—it requires continuous monitoring, education, and improvement. As cyber threats evolve, organizations must adapt their security strategies accordingly.
Best Practices to Prevent Data Leakage and Data Breaches
Preventing data leakage requires a multi-layered approach that combines technology, policies, and human awareness.
1. Implement Strong Data Security Measures
- Regularly audit systems and data access controls
- Ensure compliance with data protection regulations
- Identify and secure high-risk data repositories
2. Use Data Loss Prevention Tools
DLP tools help monitor, detect, and block unauthorized data transfers across email, cloud platforms, endpoints, and networks.
3. Monitor Access and Activity
Visibility into network activity allows organizations to detect suspicious behavior early and respond before damage occurs.
4. Apply the Principle of Least Privilege
Employees and third parties should only have access to the data necessary for their roles. This minimizes the risk of accidental or malicious data leakage.
5. Conduct Cybersecurity Awareness Training
Employees should be educated on:
- Phishing and social engineering tactics
- Safe data handling practices
- Password hygiene
- Recognizing suspicious activity
Training should be ongoing and updated regularly.
6. Delete or Archive Unnecessary Data
Old, unused data increases risk. Regularly delete outdated information or store it in isolated, secure environments.
7. Use Strong Passwords and Secure Password Management
Implement password policies that require complexity, uniqueness, and regular updates. Encourage the use of secure password managers.
8. Assess Third-Party and Supply Chain Risks
Vendors and partners often have access to sensitive data. Regularly evaluate their security practices to prevent supply chain-related data leakage.
9. Secure Employee Offboarding Processes
When employees leave, immediately revoke access to systems, devices, and data to prevent insider threats.
10. Implement Multi-Factor and Biometric Authentication
Additional authentication layers significantly reduce the risk of unauthorized access.
11. Encrypt Sensitive Data
Encryption ensures that even if data is accessed without authorization, it remains unreadable.
12. Monitor Threat Intelligence Sources
Continuous monitoring of emerging threats helps organizations respond proactively to potential risks.
Learning How to Prevent Data Leakage
Data leakage is often the first step in a much larger data breach, making prevention critically important. Organizations must take a proactive approach that combines:
- Employee education
- Strong technical controls
- Clear data handling policies
- Continuous monitoring and improvement
Building a culture of cybersecurity awareness ensures that everyone—from leadership to frontline employees—understands their role in protecting sensitive data.
Conclusion
Data leakage is one of the most persistent and dangerous cybersecurity threats in the modern digital landscape. Whether caused by human error, insider threats, or weak security controls, the consequences can be severe and long-lasting.
Preventing data leakage and data breaches requires more than just technology. It demands awareness, discipline, and a commitment to continuous improvement. By implementing strong data loss prevention strategies, training employees, securing systems, and monitoring risks, individuals and organizations can significantly reduce their exposure to cyber threats.
In an era where data is power, protecting it is not just a technical responsibility—it’s a business imperative.
FAQs
What is data leakage in cybersecurity?
Data leakage is the unauthorized exposure of sensitive information due to human error, system misconfiguration, or insider actions.
How is data leakage different from a data breach?
Data leakage is often accidental, while a data breach involves intentional theft of data by attackers.
What are the most common causes of data leakage?
Human error, weak passwords, phishing attacks, lost devices, and misconfigured systems are the leading causes.
Can data leakage be completely prevented?
While no system is 100% secure, strong data loss prevention strategies can significantly reduce the risk.
Why is data loss prevention important for businesses?
DLP protects sensitive data, ensures regulatory compliance, reduces financial losses, and preserves customer trust.
What should I do if data leakage is detected?
Act immediately by isolating affected systems, investigating the cause, notifying relevant stakeholders, and strengthening security controls.




