Cybercrime has evolved far beyond generic scam emails and obvious fake messages. One of the most dangerous and effective tactics used by modern attackers is spear phishing. Unlike traditional phishing, spear phishing is calculated, targeted, and highly personalized, making it far more difficult to detect and far more damaging when successful.
As digital communication becomes central to business operations and personal interactions, understanding spear phishing meaning, how it works, and the risks it poses is essential. This guide explains what spear phishing is, why it is so effective, how it differs from regular phishing, and what individuals and organizations can do to reduce their exposure to these targeted attacks.
What Is Spear Phishing?
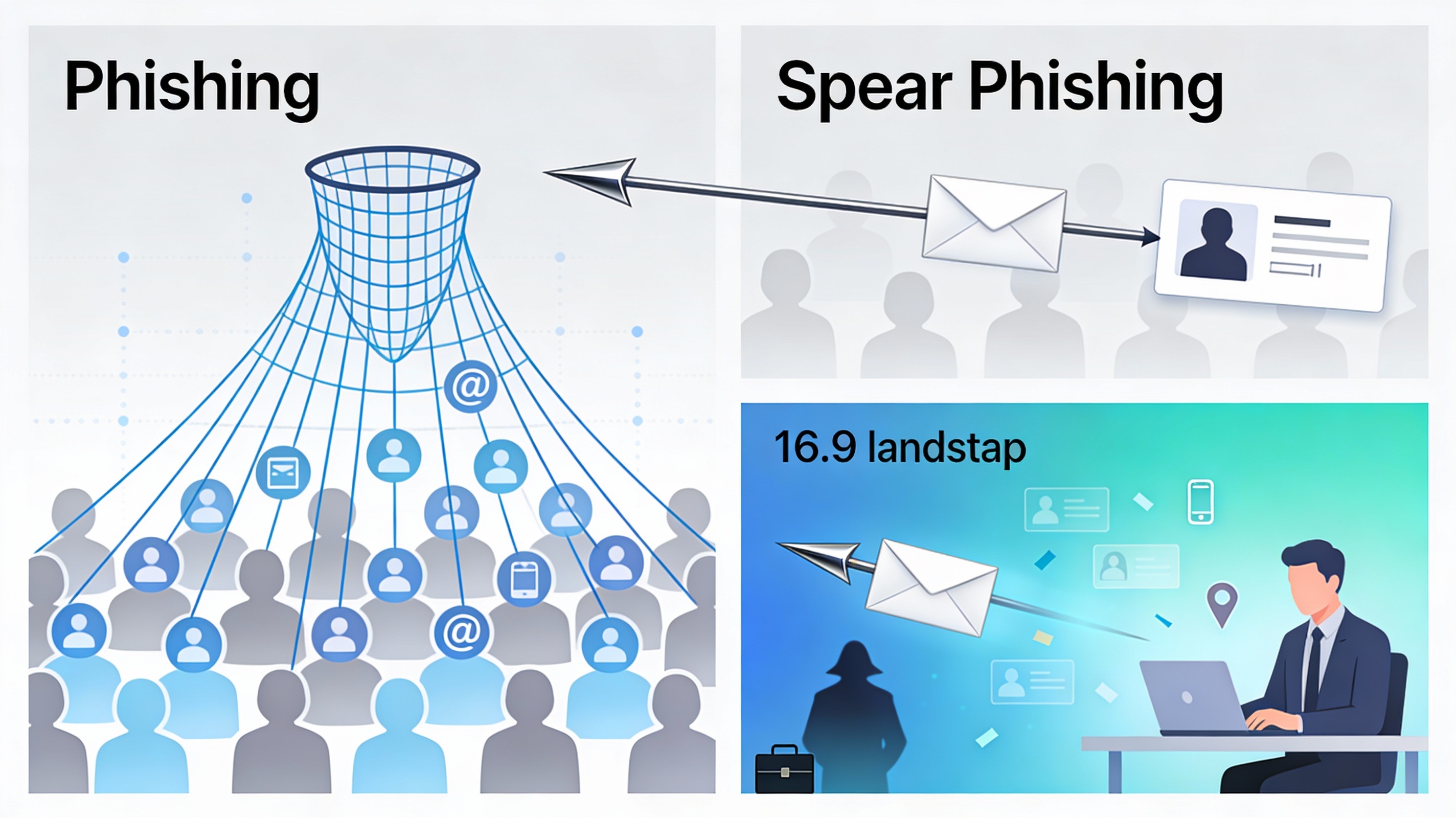
Spear phishing is a form of targeted cyberattack designed to deceive a specific individual, group, or organization into revealing sensitive information or performing actions that benefit the attacker.
To explain the spear phishing definition simply, it is a highly personalized version of phishing where attackers carefully research their target before sending a deceptive message. These messages often appear legitimate because they contain personal, professional, or contextual details that the recipient recognizes and trusts.
When people ask what is spear phishing, the key distinction lies in intent and execution. Unlike mass phishing campaigns that target thousands of users randomly, spear phishing focuses on quality rather than quantity. The attacker selects a specific target and tailors the attack to that person’s role, habits, relationships, and digital footprint.
The term spear fishing cyber is sometimes used to describe these attacks, drawing a parallel between casting a wide net and aiming a spear at a single, valuable target.
Why Spear Phishing Is So Dangerous
Spear phishing attacks are successful because they exploit human trust rather than technical vulnerabilities. Instead of breaking into systems through brute force, attackers manipulate people into opening doors for them.
These attacks often succeed because the communication appears familiar. The message may look like it comes from a manager, colleague, vendor, bank, or service the recipient uses regularly. Because the message feels relevant and urgent, victims are more likely to respond without questioning its authenticity.
Spear phishing is especially dangerous because it can bypass traditional security tools. Firewalls and spam filters may not flag these emails since they do not contain obvious malicious patterns. The real vulnerability lies in the recipient’s perception of trust.
How Spear Phishing Attacks Work
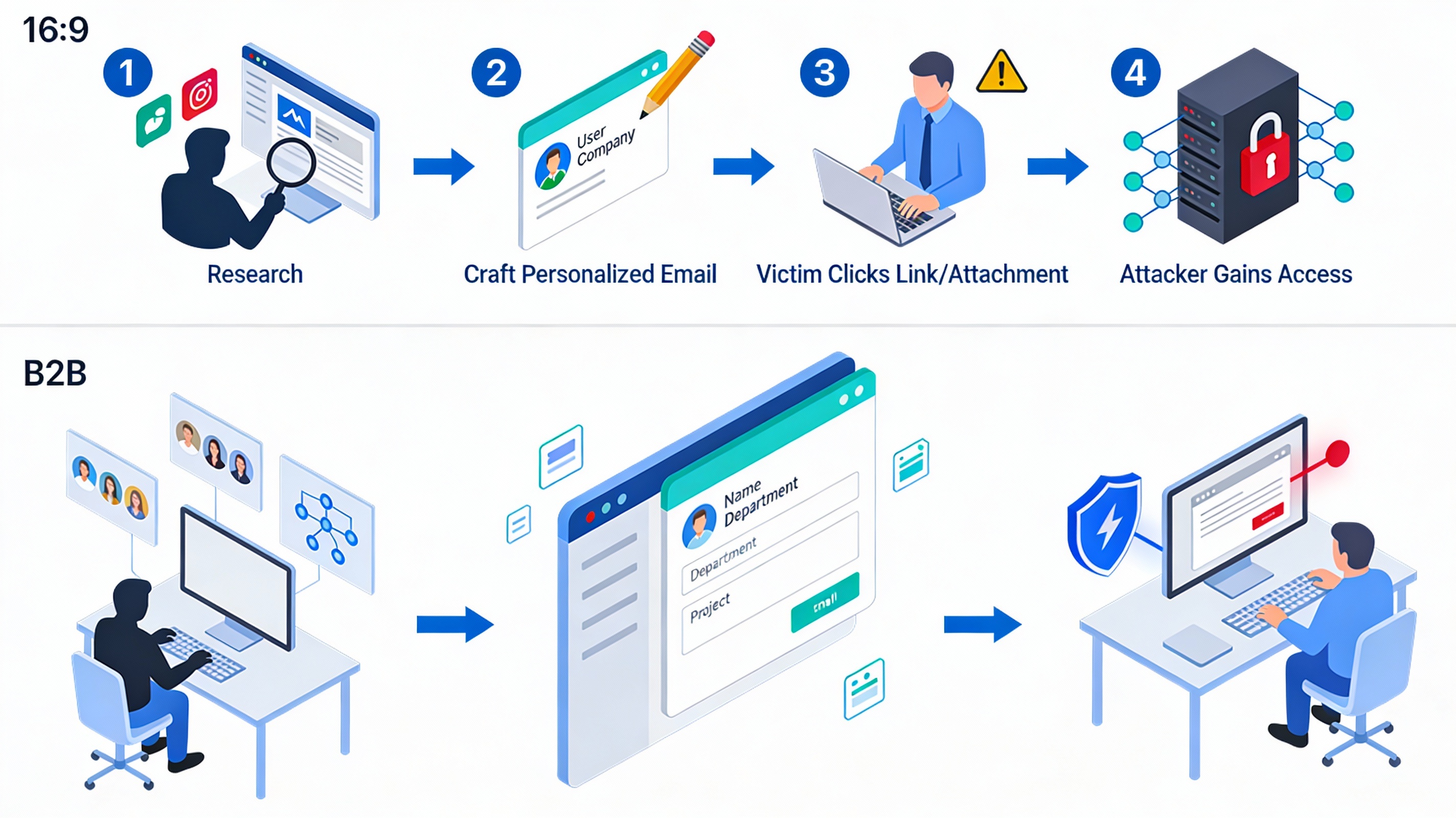
Understanding how spear phishing works is essential for recognizing and preventing it. These attacks usually follow a structured process that involves planning, research, execution, and exploitation.
The attacker begins by defining the goal of the attack. This could involve stealing login credentials, accessing sensitive company data, transferring money, or installing malware on a device.
Once the objective is clear, the attacker identifies a suitable target. High-value individuals are often selected, such as executives, finance staff, system administrators, or employees with access to confidential data.
The next step involves extensive research. Attackers gather information from publicly available sources such as social media profiles, company websites, professional networking platforms, and leaked databases. This research helps them understand the target’s job role, communication style, relationships, and routines.
Using this information, the attacker crafts a highly convincing message. This message may reference recent events, internal projects, colleagues’ names, or personal interests. The aim is to remove suspicion by making the message feel authentic.
Finally, the message prompts the victim to take action. This could involve clicking a link, downloading an attachment, replying with sensitive information, or approving a financial transaction. Once the victim complies, the attacker gains access or control, often without immediate detection.
Information Used in Spear Phishing Attacks
One of the defining features of spear phishing is the use of personal and contextual information. Attackers rely heavily on data harvested from online activity to make their messages believable.
Common sources of information include social media profiles, where users share job updates, travel plans, personal milestones, and connections. Professional networking platforms reveal job titles, company structures, and reporting relationships. Company websites provide insight into leadership teams, vendors, and ongoing initiatives.
Email addresses, phone numbers, and usernames are often collected from public directories or previous data breaches. Even seemingly harmless details such as hobbies or favorite brands can be used to create convincing pretexts.
The more information an attacker gathers, the more realistic the spear phishing attempt becomes.
Common Spear Phishing Techniques
Spear phishing attacks use a variety of techniques to manipulate victims into compliance. One common method involves fake login pages that closely mimic legitimate websites. Victims are directed to these pages and unknowingly enter their credentials.
Another technique involves malicious attachments disguised as invoices, reports, or internal documents. Once opened, these files can install malware that gives attackers ongoing access to the device or network.
Impersonation is also widely used. Attackers may pretend to be senior executives, IT staff, or trusted partners. Messages often create urgency by claiming that immediate action is required to prevent account suspension, financial loss, or operational disruption.
Emotional manipulation plays a significant role as well. Messages may evoke fear, authority, curiosity, or urgency to override rational decision-making.
Identifying a Spear Phishing Scam
While spear phishing attacks are designed to be convincing, there are warning signs that can help identify them. Messages that demand urgent action without proper verification should be treated cautiously. Requests for sensitive information such as passwords, verification codes, or financial details are a major red flag.
Suspicious sender addresses are another indicator. Attackers often use domains that closely resemble legitimate ones but contain slight variations. Poor grammar or unusual phrasing may also indicate deception, especially when the message claims to come from a professional organization.
Unexpected attachments or links should never be opened without verification. Hovering over links to inspect the destination URL can help identify inconsistencies.
Being aware of these signs can significantly reduce the risk of falling victim to spear phishing.
Spear Phishing vs Phishing
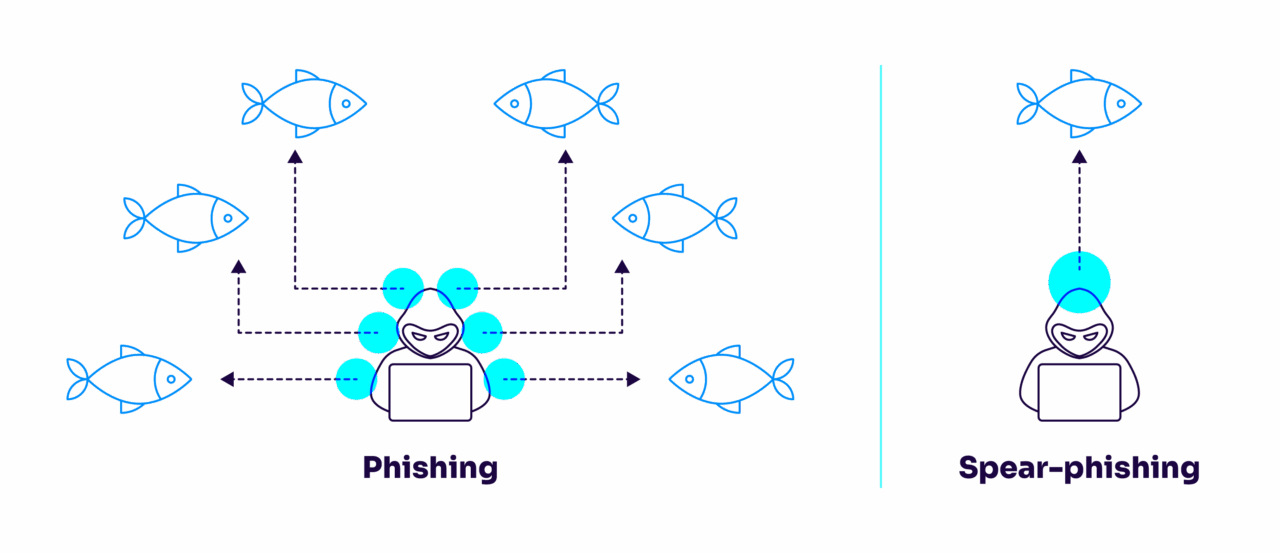
Although spear phishing is a type of phishing, there are important differences between the two. Traditional phishing attacks are broad and generic. They are sent to large numbers of recipients with the hope that a small percentage will respond.
Spear phishing, on the other hand, is targeted and personalized. Each message is crafted for a specific recipient, increasing the likelihood of success. This focus on precision is what makes spear phishing more dangerous and harder to detect.
While phishing relies on volume, spear phishing relies on research and deception.
Related Targeted Phishing Attacks
Spear phishing is closely related to other targeted attack types. One such variant is whaling, which targets high-profile individuals such as executives, board members, or public figures. These attacks often involve large financial stakes or access to sensitive organizational data.
Another related threat is Business Email Compromise. In these attacks, criminals impersonate company executives or compromise legitimate email accounts to trick employees into transferring money or sharing confidential information.
All of these attacks share a common reliance on trust, authority, and social engineering.
Who Is Most at Risk from Spear Phishing
Although anyone can be targeted, certain individuals face higher risk. Executives and decision-makers are prime targets due to their authority and access. Employees in finance, human resources, and IT departments are also frequently targeted because of their roles.
Organizations within supply chains are increasingly targeted as attackers look for weaker entry points into larger networks. Even individuals with strong security awareness can be deceived if the attack is convincing enough.
Impact and Risks of Spear Phishing
The consequences of spear phishing can be severe. Financial losses may occur through fraudulent transactions or theft. Stolen credentials can lead to data breaches, intellectual property theft, or system compromise.
In some cases, malware installed through spear phishing can create long-term access for attackers, allowing them to monitor activity or launch further attacks. Reputational damage and loss of trust can be just as damaging as financial losses, especially for businesses.
Challenges in Detecting Spear Phishing
One of the greatest challenges in defending against spear phishing is its subtlety. Because these attacks are tailored and often mimic legitimate communication patterns, they can evade automated detection tools.
Human error remains the weakest link in cybersecurity. Even well-trained individuals can make mistakes under pressure or when faced with convincing messages.
This makes continuous awareness and vigilance essential components of defense.
How to Prevent Spear Phishing Attacks
While no solution can eliminate the risk entirely, there are effective measures that can reduce exposure. Security awareness training helps individuals recognize red flags and respond appropriately. Verifying requests through secondary channels can prevent fraudulent actions.
Strong authentication practices, such as multi-factor authentication, reduce the impact of stolen credentials. Monitoring account activity and implementing strict access controls can limit damage if an attack succeeds.
A proactive security culture is one of the strongest defenses against spear phishing.
Why Awareness Matters More Than Ever
As attackers refine their techniques, spear phishing attacks will continue to grow in sophistication. Technology alone cannot solve the problem. Awareness, critical thinking, and verification play a central role in prevention.
Understanding spear phishing meaning and recognizing how these attacks operate empowers individuals and organizations to protect themselves more effectively.
Conclusion
Spear phishing represents one of the most serious threats in modern cybersecurity. By combining research, personalization, and social engineering, attackers can bypass traditional defenses and exploit human trust.
Understanding what is spear phishing, how it works, and the risks it poses is essential in today’s digital environment. While these attacks are difficult to detect, informed users and proactive security practices can significantly reduce the likelihood of success.
In a world where information is currency, protecting trust is just as important as protecting systems.
FAQs
What is spear phishing in simple terms
Spear phishing is a targeted scam where attackers personalize messages to trick specific individuals into sharing sensitive information or performing harmful actions.
How is spear phishing different from phishing
Phishing targets large numbers of people with generic messages, while spear phishing targets specific individuals with highly personalized communication.
Who is most vulnerable to spear phishing attacks
Executives, finance teams, IT staff, and employees with access to sensitive data are common targets, but anyone can be affected.
Can spear phishing be completely prevented
It cannot be eliminated entirely, but awareness, verification, and strong security practices can greatly reduce the risk.
What should you do if you receive a suspicious email
Do not click links or download attachments. Verify the request through a trusted channel and report the message according to your organization’s security policy.




